In Part 1 of this blog series we explored what CBDC, or Central Bank Digital Currencies are, and why they are important. Successful completion of CBDC projects requires the involvement of multiple partners. There are several key features CBDC has to implement and Thales can help with a few: Security, Offline CBDC and digital ID wallets.
The end user drives the use case, the use case drives the partner selection
To gauge the extent of partnerships required it is important to consider all stakeholders that stand to benefit from any particular use case. McKinsey define innovation as “the systematic practice of developing and marketing breakthrough products and services for adoption by customers”. ‘Development’ and ‘breakthrough’ are handled by technology stakeholders. However, these CBDC technology stakeholders should recognise that success is in sustained “adoption by customers”, not just in releasing new products. The table below shows examples of real world CBDC use cases being explored globally with customer requirements at their heart; also shown are the ecosystem partnerships involved highlighting the variety of stakeholders required:
| Use Case | Country/Region | Ecosystem partnerships |
|---|---|---|
| Construction Supply Chain Payments2 | Australia | Master builders, contractors, consumer, Web3 technology lab, open source ledger provider, central bank |
| Livestock Auction2 | Australia | Wealth management and private equity companies livestock farming organisations, central bank |
| Goods and Services Tax2 | Australia | Commonwealth bank, accounting software vendor, central government, private enterprises, University research units, consumers |
| Offline Payments for Universities2 | Australia | Regional commercial bank, consulting company, open source ledger provider, Thales, two universities, students, smart card provider, merchants |
| Consumer retail purchases | Sweden | Central bank, car dealership, consumer, consulting company, legal firm, distributed ledger platform, regional banks, wearable providers |
| Cross-border transactions, wholesale interbank system and retail e-Wallet3 | UK, Hong Kong | Nation State monetary authority, Science and Technology Research Institute, central bank |
Security ecosystem partnerships
As with cash and online payments, CBDC are targeted for fraud and susceptible to risks. These risks need to be identified, anticipated, mitigated and managed. When digital cash sits on a secure device, the loss, theft or mistreatment of that device means that real cash is lost. In CBDC systems, the ‘cash’ is usually represented in the form of a token. A token, is an object of value transferrable to the receiving party, which should be able to verify its genuineness. In the CBDC world, we define a token as a cryptographic signature that represents a certain value of digital currencies.
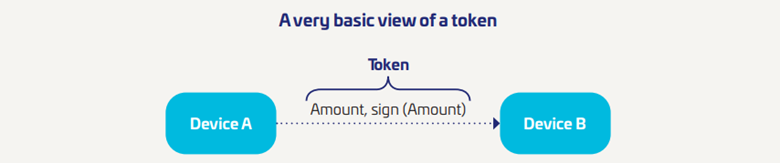
In order to prevent fraudulent creation of digital money, tokens must have at a minimum the following characteristics:
- They should not be forgeable. It should be very difficult for a fraudster to create a genuine token.
- They should not be re-usable: a token should represent a single transfer of digital money for a certain amount to a particular payee.
Broad security and resilience considerations
No CBDC project, initiative or national rollout is an island. Bridges need to be built for resilience and for security reasons. Connections with security technology providers, industry experts, regulators and foreign jurisdictions are just a sample. Let’s take a look at security issues that will affect your CBDC security strategy and choice of partnerships:
- Device security: offline payments rest entirely on a device, whether phone, card, vehicle or wearable. What are your security considerations for these devices? For example, working with the secure element of a mobile phone.
- Monitoring and detection: device security mechanisms, including the secure element, could be breached. A bad actor could obtain a genuine private key through this process and, subsequently, generate fake tokens, no different to printing their own physical cash. A monitoring and detection system should be able to identify fake tokens, double spending, track digital currency in circulation, detect money laundering patterns, plus identify the source of breaches at device level.
- Data privacy; e-wallets, devices and transaction systems should not have direct access to sensitive personal data. However, in some circumstances, the institutions handling money as part of a retail transaction should have the ability to perform KYC (Know Your Customer) checks, as mandated under their industry compliance regime. For example, if a consumer offers to deposit €100,000 of CBDC into a bank, the digital cash on the device doesn’t care who is carrying it. However, the bank absolutely needs to know who’s paying in an amount of this size. Another dimension is that financial limits need to be set up, to prevent such large sums accruing while simultaneously maintaining data privacy. PCI DSS, GDPR and local country data privacy regulations still apply in addition to money laundering regulations such as AML5, Anti Money Laundering Directive (EU) 2018/843.
- Data security and transaction security: CBDC pilots globally are considering security-by-design principles. This brings into scope independent software vendors, such as Thales, for data-at-rest, data-in-motion and data-in-use protection. Encryption key management lies at the heart of digital asset custodianship, of which CBDC is a subset. Protecting these requires robust key lifecycle management from creation to destruction. The process should be automated, scalable, and meet global standards (NIST, EAL, Common Criteria, FIPS). Some national programs are founded on the principle of financial sovereignty. The concept of data sovereignty aligns with this principle. As such, all technology partners should subscribe to established best practice the areas of data governance, user access management, key management, code signing, secrets management, encryption and tokenisation. For transaction validation, the payee must be sure that the payer is transferring legitimate digital currencies, signed by a legitimate private key. The payer must be sure that the payee SE is not a counterfeited secure element so that there is no loss of digital currencies. Mutual authentication occurs between secure elements that have been provisioned to devices securely during manufacture.
- Infrastructure security: secure elements and other crypto hardware devices within the infrastructure need to be assessed for risk of side channel attacks (sniffing, emission analysis, power consumption analysis). Also power and temperature-based attacks. Protection for devices may include shielding, plus onboard security for applications and operating systems.
- Quantum agility: token generation may rely on public key cryptography. In this instance, are partners in your proposed supply chain prepared for quantum agility?
- Resilience: security of transactions during a network, power or system outage. Digital Operational Resilience Act (DORA) is relevant to financial institutions looking to partner in this space. As with other initiatives reliant on technology, financial institutions must follow rules for the protection, detection, containment, recovery and repair capabilities against ICT-related incidents.
Planning for the resilience of CBDC payment systems during network, power or system outages is an obvious consideration, yet offline capability was previously missing from some national project scopes. It’s an area we’ll examine right now.
Offline CBDC and partnerships
Offline CBDC is key for replacing cash. The Thales Banking and Payments business has created a Thales solution for the Offline CBDC that is being discussed with many National Banks in their CBDC investigations. An offline payment consists in the payer device generating one or more token(s) and sending the token(s) to the payee device where they are verified and stored.
Advantages of Offline CBDC payments
- Offline payments facilitate transactions even when networks, systems, and power grids are down.
- They also support the use of cheaper, less connected devices, such as smart cards or passive wearables, for financial inclusion. Valuable in both emerging economies with large numbers of underbanked citizens, and advanced economies with regions of persistent poor telecoms coverage.
- No new hardware (phones, cards etc.) need necessarily be developed because it exists in the market today.
- Offline payments act as a mechanism to absorb traffic, and not overload the online system.
- POC and workshop programs exists to demonstrate the overall solution including:
- Card prototype for offline payment with phone (software implementation in phone).
- Server supporting the online transactions (with hardware security module simulation for POC demo or HSM-as-a-Service for pilot environments).
- Confidential Computing platform managing the Monitoring and Detection System.
- Finally, only Offline CBDC payments can offer a level of convenience and privacy similar to cash.
CBDC offline payment pitfalls to avoid
Instant settlement between devices is strongly preferable. Just like cash in a physical wallet, digital cash is stored in devices and moves from one device to another. Devices are not intended to become a ledger of IOUs. A chain of offline payments cannot go on forever, at some point they must be offloaded onto the online system to stay within AML limits and reduce the risk and magnitude of potential fraud.
Security should be designed into the program from the outset as described above. Take notice of items specific to offline CBDC. For example, the monitoring of the amount of digital money in circulation offline, to detect any fraudulent generation of digital currency, double spending.
Certificate and encryption key lifecycle management form the bedrock of all ‘grown up’ digital asset custodianship projects of which CBDC is a subset. Many digital asset startups and scaleups exist, for partnering in this space, but many operate with immature crypto security regimes. Their ambitions to link with major financial institutions, such as central banks, regional commercial banks, or government, are subject to strict scrutiny of supply chain security. Measures such as intelligent key lifecycle management and secure automated business logic approval frameworks help support their ambitions and aid the progression of CBDC projects.
Resilience measures for offline CBDC include planning for the handling of transaction failures emanating from loss of proximity or communication channel between devices, or device battery drainage. Make contingences for lost or stolen devices.
Offlne CBDC advantages are highlighted in reports by the Bank for International Settlements and are being considered by the European Central Bank and most other central banks. Thales and it’s wide ecosystem of consulting, system integrator, ledger an d financial partners can deliver offline CBDC payment pilots around the globe.
Here comes The Wallet
One of the trends in Cybersecurity is the use of Self-Sovereign Identities (SSI). This refers to a digital identity that is owned and controlled by the individual to whom it belongs.
With a digital ID wallet, individuals have the same level of control over their identity as they do with a physical wallet. They can use their documents, such as identification cards, whenever they want without the need for a third party, like the government, to prove their identity.

Thales Digital Identity and Security business has created a Thales Digital ID Wallet which recently became the first mobile Driver License (mDL) provider in the world to receive UL Solutions’ independent certification for meeting the ISO/IEC global standard.
Most of the Digital ID Wallets have a vision of supporting also payments so in the future such wallets will be perfect for combination with Online and foremost Offline CBDC.
Thales is participating in the multinational NOBID consortium. Goal of NOBID is developing a large-scale pilot for the payment use case in the EU Digital Wallet, sponsored by the European Commission.
Thales and CBDC
Thales has more than 40 years of experience with data security and security of payment transactions. We help secure from small to F100 enterprises with data security. In the Payments area we help over 3,000 financial institutions, retailers, and other organizations address the challenges of payments.
Thales provides the root of trust and all core encryption elements for any modern infrastructure. We Protect our Customers with innovative and proven Thales CPL products and solutions like data discovery, data encryption, key management, network encryption, hardware security modules and data protection on demand solutions, SaaS platforms for data security.
Additionally, Thales has a large global Partnerhip Program to complement our products with a wide range of solutions and services. Partnerships range from Technology Partnerships for integration of our products to cooperation with major Global System Integrators (GSI).
Technology Partners provide CBDC solutions like Blockchain, Ledger, Payment processing, Mobile Wallets and GSI are able to run large-scale projects like CBDC where advisory and implementatiton services are required.
CBDC as an example has cross-border requirements.
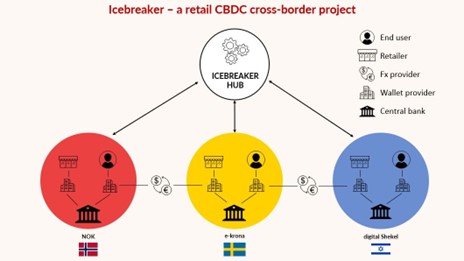
Cross-border CBDC, Bank of International settlements.
It is important to recruit vendors with global partrnerships, because CBDC projects do not end in a single market.

 Ollie Omotosho | Director, Global Strategic Partnerships
Ollie Omotosho | Director, Global Strategic Partnerships