Crypto Command Center - Product Brief
Centralize your crypto management HSM resources and reduce IT security infrastructure costs with Thales Crypto Command Center.
![]() It is common to deploy encryption for the protection of sensitive and personal information in order to meet compliance needs. The security level of any encryption solution often comes down to the security of the encryption keys. And storing the keys in special-purpose hardware, such as a Hardware Security Module (HSM) is recommended by experts as a best practice
It is common to deploy encryption for the protection of sensitive and personal information in order to meet compliance needs. The security level of any encryption solution often comes down to the security of the encryption keys. And storing the keys in special-purpose hardware, such as a Hardware Security Module (HSM) is recommended by experts as a best practice
However, until now hardware encryption solutions have not provided the agility and flexibility needed in virtualized and cloud environments. Rolling out a virtual application that requires encryption, signed digital certificates, or other PKI functions can often add days or weeks to a project.
Consolidate your enterprise key vaulting and PKI services by moving away from physical HSMs to virtualized HSMs, with Crypto Command Center - the cloud's first high-assurance key vaulting solution.
Likewise, Service Providers can add high-value key-vaulting and PKI services to their hosted and cloud offerings that allow them to administrate the HSMs but never access their customers’ keys.
Security administrators can create a centralized pool of high assurance cryptographic resources that can be provisioned out to the people and lines of business in their organization that need them.
Administrators set up crypto service templates with predefined HSM capabilities, which users can then leverage to provision services in a standardized and compliant manner. Crypto resources can be provisioned on demand for one to thousands of HSMs simultaneously. Additionally, administrators can monitor crypto resources, generate dynamic reports, and always be up to date on the status of their HSM appliances. Having a convenient, centralized view across the device pools provides visibility into the status and health of resources, and enables administrators to be proactive in dealing with challenges before they affect service level agreements.

"CA Technologies relies on Thales's capabilities to deliver high assurance versions of Privileged Access Manager, the company’s privileged identity management platform... Crypto Command Center has the potential to be a game-changer in the way we employ crypto resources. Privileged Access Manager protects very large hybrid-cloud enterprises and the ... Crypto Command Center design is right in line with Privileged Access Manager’s architecture and our customer scalability, cost and security requirements"
- Mordecai Rosen, Senior Vice President, Operations at CA Technologies
In addition to our Premium license version that offers full provisioning and monitoring capabilities, you can also test drive Crypto Command Center with our Freemium License. Easily install and sample the software in a non-production environment to determine how you too can benefit.
Dramatic cost savings. Not only can your hardware requirements be reduced by as much as 95%, but Thales's automation processes saves hours of work for each cryptographic resource.
Simplified management and administration. Self-service and encryption templates mean that crypto expertise isn't required for crypto rollouts anymore.
Fewer security gaps. Centralized crypto expertise results in security and encryption policies that are enforced consistently across the enterprise.
Fast rollout. Now an enterprise can implement encryption in a new application in minutes, not hours.
Proven Solution. Built on the market leading Thales Luna Network HSMs which currently provide protection for over $1 trillion in daily financial transactions.
Improved Visibility. Through crypto resource reporting and monitoring.
Lower Total Cost of Ownership (TCO). Share resources and reduce costs with multi-tenancy and role separation.

A crypto hypervisor revolutionizes the delivery of encryption. IT departments can now deliver on-demand, elastic crypto services for data protection—in minutes, not days. Our crypto hypervisor is the combination of Crypto Command Center together with the proven Thales Luna Network Hardware Security Modules (HSMs).
For the first time, high-assurance encryption services fit the cloud operations model. Now the full cost and innovation advantages of virtualization can be exploited without compromising security or compliance.
Admin- & User-Friendly Cryptography: IT maintains full, centralized control of the delivery of encryption services. Users have full control of their cryptographic resources knowing that other tenants and administrators cannot access their encryption keys.
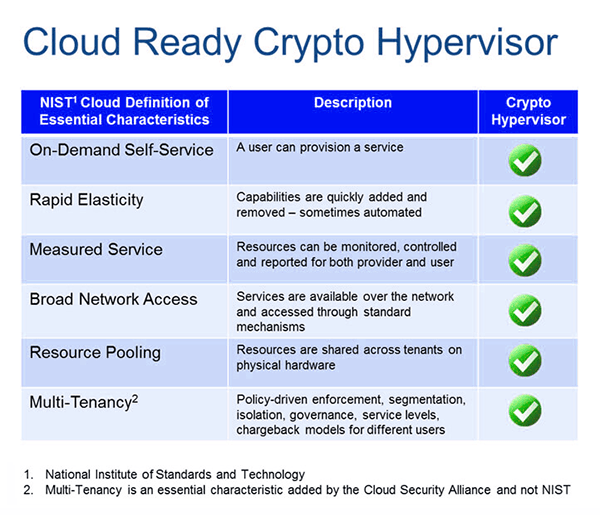
As a leader in the security market, Thales is focused on bringing strong, innovative security solutions to next-generation environments like the cloud. Powered by the Crypto Command Center and Luna Network HSMs, our crypto hypervisor represents the culmination of years of research and development:
Centralized Crypto Management. Administrators can manage single or groups of virtual HSMs, and publish a list of on-demand service templates for their users. These templates are easy to navigate, and users are only offered services that they have permission to initialize.
Virtualized Crypto Hardware. SafeNet Crypto Command Center abstracts HSMs into many dynamic crypto resources that maintain access controls and user experience as if each resource were a dedicated physical HSM. Establish an environment in which many organizations can leverage the same hardware without fear of keys being lost or stolen by other tenants, with mutli-tenancy. Even administrators will not be able to access the users’ keys.
Monitor crypto resources. Generate dynamic reports, improve visibility, and always be up to date on the status of your HSM appliances with a centralized, convenient view of the device pools.
Separation of Roles and Responsibilities in Multi-tenant Environments. Users maintain access to their key material while the central authority sets overall security policies.

Centralize your crypto management HSM resources and reduce IT security infrastructure costs with Thales Crypto Command Center.