We all make misteaks.
However, some mistakes are bigger than others. A misplaced typo is one thing, but a single employee falling for a phishing attack, giving hackers inside access to the business network of a major organization, where they can cause catastrophic damage to the network and leak personal data, lighting up social media and causing immense reputational damage, which destroys the trust of customers and causes the share price to plummet? Well, that’s a much bigger problem.
Yet, around the world, phishing attacks designed to create this scenario are launched every minute, every hour, every day.
The simple truth is that in today's interconnected digital landscape, the constant threat of cyberattacks looms over businesses and individuals alike. Among these threats, phishing attacks stand out as one of the most dangerous and prevalent tactics used by cybercriminals. The need for robust cybersecurity measures has never been more critical, especially as the sophistication of phishing attacks, and other forms of identity theft, continue to evolve.
The following article will take a closer look at the rising threat, the benefits of FIDO2 authentication, the rapidly changing regulatory landscape, and the different types of passkeys.
The escalating threat landscape and the rise of phishing attacks
Cyberattacks have surged exponentially in recent years, with phishing attacks being a primary weapon in the arsenal of malicious actors. Statistics paint a stark picture of this escalating threat:
- In Q1 2025, the total number of phishing attacks exceeded 1M, which is the largest reported since 2023.
- About 3.4 million phishing emails are sent every day globally
- In 2024, the FBI's Internet Crime Complaint Center (IC3) received around 850,000 complaints of suspected internet crime, marking a 33% increase from 2023.
- According to the Thales Passwordless 360 ebook, 31% of breaches in the last decade involved stolen credentials.
- The 2025 Thales Data Threat Report confirmed that phishing moved up from third to second position among the most observed attacks, overtaking ransomware.
Phishing attacks not only jeopardize sensitive company data but also external user information, leading to reputational damage and loss of customer trust. Traditional security measures, such as relying solely on passwords, have proven inadequate in combating the growing sophistication of phishing attacks. This is where FIDO2 and Multi-Factor Authentication (MFA) can step-in as a potent solution.
FIDO2 Authentication and MFAs: A robust defense against phishing attacks
The FIDO2 standard is intended to solve multiple user scenarios and provides passwordless, cryptographic tokens. A FIDO2 authenticator, also known as a FIDO security key, embeds one or more private keys, each dedicated to one online account.
The protocols require a “user gesture” - a touch, a PIN, or a biometric - before the private key can be used to sign a response to an authentication challenge.
FIDO2 security keys can entirely replace weak static password credentials with strong hardware public/private key credentials.
FIDO2 Benefits:
Security: Unique login credentials across every website, which are never stored on a server, eliminating the risks of phishing, all forms of password theft and replay attacks.
User experience: Users login with simple built-in methods on their devices, or by leveraging easy-to-use FIDO2 security keys.
Privacy: Unique keys for each internet site that cannot be used to track users across sites. Biometric data, when used, never leaves the user’s device.
Scalability: Enable FIDO2 through a simple JavaScript API call that is supported across all leading browsers and platforms.
Multi-Factor Authentication is a security mechanism that requires users to provide two or more forms of verification before granting access to an account. This extra layer of security greatly reduces the success rate of phishing attacks. Unlike traditional single-factor authentication, where only a password is required, MFA's multi-layered approach thwarts phishing attempts effectively.
Emerging trends in access management and the regulatory landscape
In response to the escalating cyber threats, regulatory bodies around the world are advocating for stronger security measures. In the EU, the General Data Protection Regulation (GDPR) emphasizes the need for organizations to implement appropriate security measures, which MFA comprehensively addresses.
In the US, the Executive Order 14028 on improving the nation’s cybersecurity requires Federal agencies to use phishing-resistant MFA based on FIDO or PIV.
This has seen FIDO2 authentication gain further prominence, leading to a surging demand for stronger security solutions, such as passkeys.
So, what exactly are passkeys?
Based on FIDO standards, passkeys are a replacement for passwords that provide faster, easier, and more secure sign-ins to websites and apps across a user’s devices. Unlike passwords, passkeys are always strong and phishing-resistant.
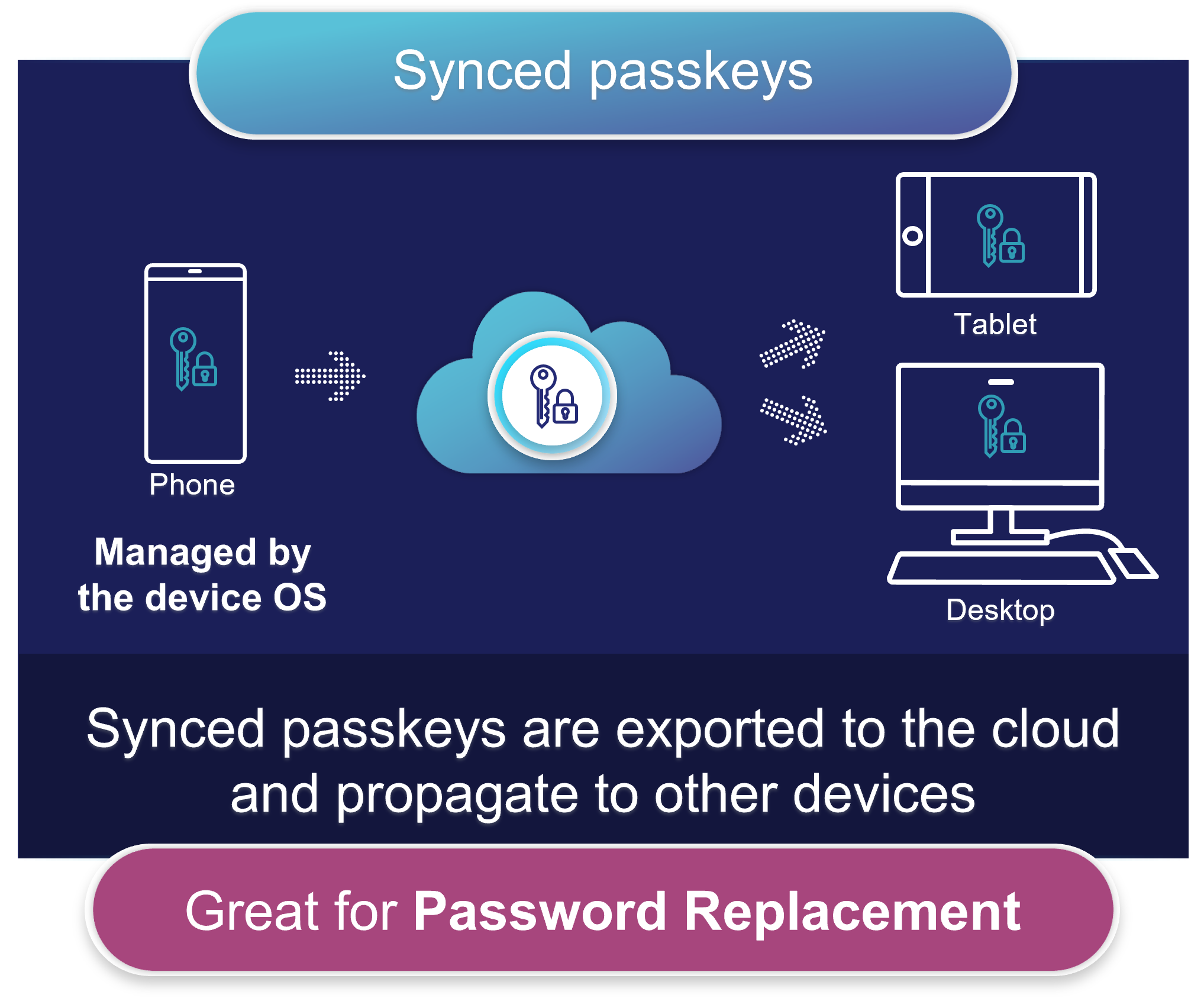
When it comes to passkeys, we need to clarify a little bit. There are, in fact, two distinct types – synced passkeys and device-bound passkeys.
Synced passkeys can be exported to the cloud and propagated to other devices. Synced passkeys simplify account registration for apps and websites, work across most devices, and can even work on other devices, simply by being within physical proximity. They are useful as a password replacement, allowing users to login to different sites and apps with a simple PIN or biometry.
Device-bound passkeys, on the other hand, require the user to have a specific device with them to gain access; however, they offer greater levels of protection against various types of cyberattacks due to the fact the private key never leaves the device.
Synced passkeys are going mainstream
Unveiled in 2022 by major tech companies including Apple, Google and Microsoft, synced passkeys are quickly growing in popularity because they are stored on the cloud and, once created, can be synchronized and used on laptops, phones and other devices. This means users no longer have to remember numerous different passwords.
The Google passkey is a good example. Users can sign-in to their Google Account with a fingerprint, face scan or device screen lock, like a PIN, which provides an additional verification method when making sensitive changes.
Apple is also beginning to focus on passkeys. Starting with iOS 17, iPadOS 17, and macOS Sonoma, users with an Apple ID will automatically be assigned a passkey, allowing them to sign into their Apple ID with Face ID or Touch ID, instead of having to use their password.
Synced passkeys are growing in popularity due to their convenience, but they are less secure than device-bound passkeys and can open the door to other types of attacks. As of today, synced passkeys are not considered to be true MFA by many cybersecurity agencies and are not compliant with some regulations (such as PSD2).
Device-bound passkeys offer greater security and compliance.
Device-bound passkeys, as the name suggests, are passkeys that exist on a single device, such as mobile phones, USB tokens or smart cards. Passkeys that are bound to a USB token or smart card are also known as ‘security keys’.
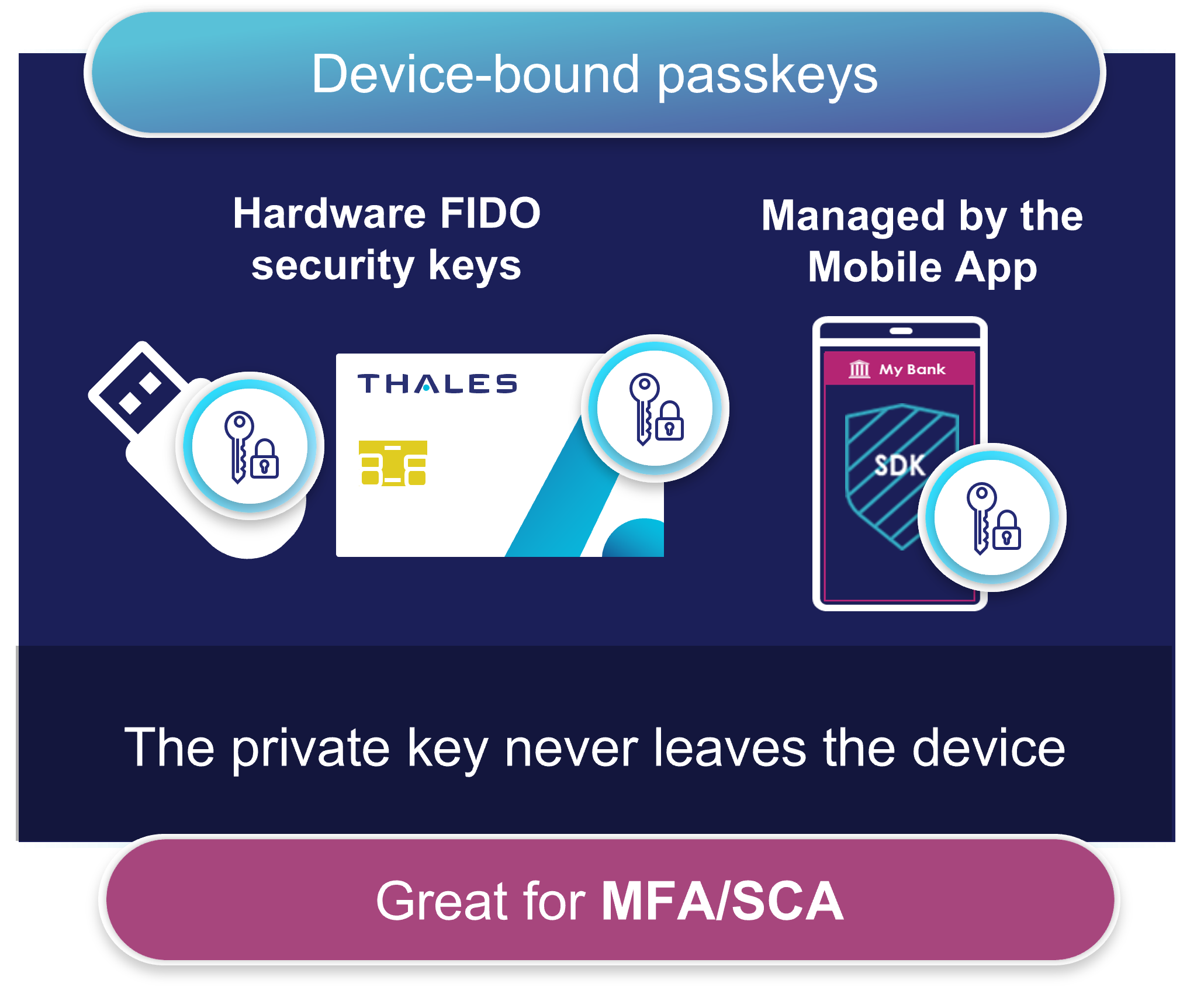
Examples of device-bound passkeys, such as the Thales FIDO and FIDO2 devices, are gaining attention due to their immunity to phishing and Man-In-The-Middle attacks, by providing an extra layer of security that even the most convincing phishing website cannot replicate.
These universal FIDO security keys are available in smart cards and both USB-A and USB-C form factors, allowing users to effortlessly authenticate from either a laptop or a mobile phone using a single device-bound passkey.
What is the best type of passkey?
So, which type is best? The answer, as usual, is “it depends”. If you’re looking for a convenient way to replace passwords for your customers, then synced passkeys will do the job.
However, if you’re looking for a truly secure method for your workforce and partners to eliminate, in addition to phishing, the threat of Man-In-The-Middle Attacks, If you need to achieve high levels of identity assurance and meet regulatory requirements, then device-bound passkeys provide a stronger layer of security and compliance with regulations such as US Executive Order or PSD2.
Fortifying against phishing with FIDO2 and MFA
As phishing attacks continue to intensify, both in number and sophistication, a more proactive approach to cybersecurity is required.
While synced passkeys offer convenience and are useful for organizations wanting to go passwordless, they simply don’t offer the robust security required for professional environments and sensitive operations, like authorizing bank transactions.
Strong phishing-resistant MFA, provided by device-bound passkeys, such as FIDO hardware security keys or FIDO mobile authenticator, is mandatory for organizations who need to protect access to sensitive resources, comply with market regulations and secure their organizations' data and user information.
By embracing these advanced MFA solutions, IT professionals can stay one step ahead in the relentless arms-race against phishing attacks and cyber threats.

 Sarah Lefavrais | IAM Product Marketing Manager
Sarah Lefavrais | IAM Product Marketing Manager