Vormetric Transparent Encryption for Teradata Database
By aggregating enormous volumes of enterprise data in Teradata database environments, organizations can derive new insights and strategic value from their data. However, these environments with big data volumes and complexity require extremely high performance.
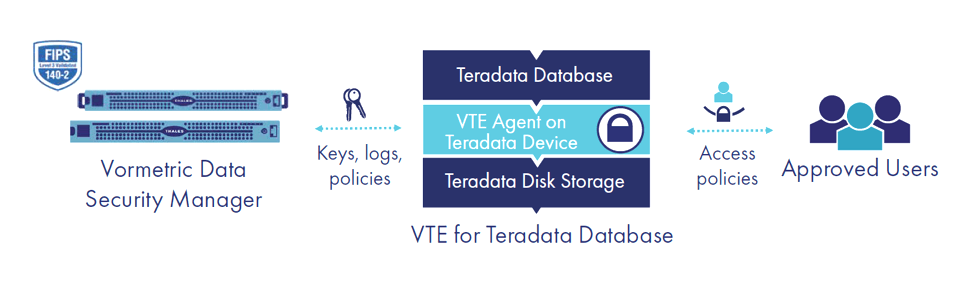
Vormetric Transparent Encryption for Teradata Database provides the highest levels of data protection while preserving Teradata performance. This solution simplifies the process of securing sensitive records, with file system-level encryption backed by centralized key management, privileged user access controls, and detailed data access audit logging, making it fast and efficient to employ robust data-at-rest encryption in Teradata environments, on premises, or in the Teradata cloud.
- Benefits
- Features
Secure Sensitive Data while Preserving Teradata Performance
Vormetric Transparent Encryption for Teradata Database enables efficient block-level encryption in Teradata databases while harnessing the high performance that is required to support processing intensive big data workloads.
Simplify Data Security Administration
Vormetric Transparent Encryption for Teradata Database works seamlessly with the Vormetric Data Security Manager, so you can centrally manage keys and access policies for encryption products from Thales and other vendors.
Easy to Deploy
Vormetric Transparent Encryption for Teradata Database addresses data security compliance and best practice requirements with minimal disruption, effort, and cost. The implementation is seamless and keeps both business and operational processes working without changes even during deployment and roll out.
Granular Access Controls
Role-based access policies control who, what, where, when and how data can be accessed. Easily implement privileged user access controls to enable administrators to work as usual, but protect against users and groups that are potential threats to data.
High Performance Encryption Solution
Organizations can harness the high-performance encryption to secure their big data workloads. The agent-based deployment model eliminates the bottlenecks and latency that plague legacy proxy-based encryption solutions.
Boost security without compromising the value of big data analytics
Identify and stop threats faster with detailed data access audit logs that not only satisfy compliance and forensic reporting requirements, but also enable big data security analytics.



