Fortaleça automaticamente a segurança e simplifique a experiência do usuário
Os métodos de autenticação tradicionais são inadequados face ao cenário crescente de ciberameaças. Os ataques automatizados cada vez mais sofisticados imitam o comportamento humano para enganar as ferramentas normais de detecção de bots. Os sistemas de autenticação com base no risco (RBA) são definidos para detectar comportamentos fraudulentos, avaliando e respondendo dinamicamente ao nível de risco de cada tentativa de login. Fortaleça suas defesas integrando várias técnicas de autenticação e biometria comportamental e introduza o nível adequado de segurança em cada jornada de autenticação.

Mais segurança
Identifique a evolução das ameaças e adapte as medidas de segurança com base no nível de risco identificado

Melhore a experiência do usuário
Ajuste dinamicamente os requisitos de autenticação sem interrupções desnecessárias

Conformidade com regulamentos
A RBA tornou-se uma solução essencial para proteger os clientes, especialmente em setores altamente regulamentados como o setor bancário
Serviços bancário em nuvem: por que a autenticação baseada em risco é vital para as instituições financeiras?
À medida que mais consumidores usam serviços bancários digitais, eles esperam poder acessar facilmente às instituições financeiras (IF) utilizando a RBA.

Equilíbrio certo entre segurança e conveniência
Melhore a experiência e a segurança do usuário e otimize a detecção de fraudes com a solução de gestão de riscos IdCloud.
COMO A THALES PODE AJUDAR
O que significa autenticação baseada em risco?
A autenticação baseada em risco (RBA) é uma abordagem de identificação inteligente que avalia vários fatores, como o comportamento do usuário, as caraterísticas do dispositivo e o contexto ambiental, para determinar o nível de risco de uma tentativa de login. Esse serviço realiza automaticamente uma avaliação do risco de um cliente e determina o risco de ameaça com base nessas caraterísticas, incluindo o endereço IP de um usuário, a localização física, o histórico de navegação etc. Esse método de autenticação proativo permite que as empresas adaptem suas medidas de segurança com base no risco percebido.
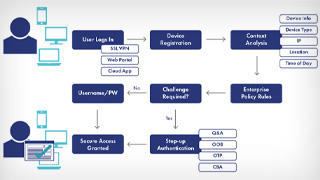
Como a autenticação baseada em risco funciona?
Ao integrar nossa solução de autenticação baseada em risco na sua jornada de autenticação, o nível de risco de cada transação do cliente é analisado. As recomendações para o método de autenticação mais adequado são então fornecidas automaticamente, reduzindo a fraude de sequestro de conta (ATO). Com a autenticação baseada em risco, podem ser definidas políticas continuamente adaptáveis com base na segmentação de clientes, preferências e casos de uso. Estas capacidades de autenticação RBA funcionam silenciosamente em segundo plano para garantir a melhor experiência para o usuário final.
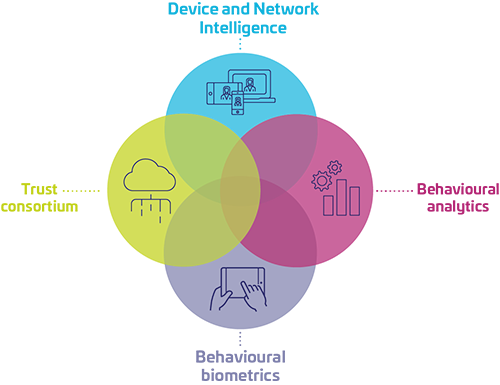
Vantagens da RBA para empresas e usuários finais
Detecção em tempo real
Identifique atividades anormais antes que elas resultem em fraude.
Com a nossa solução em tempo real, as ameaças são bloqueadas à medida que tentam acessar seu ambiente.
Segurança personalizada
Seu tráfego, suas regras.
Ajudamos a proteger seu ambiente de acordo com seus termos. Automatize as ações que pretende com base nos níveis de risco e nos limiares de risco dos seus usuários.
Segurança multicanal
Tenha todos os dispositivos sob controle.
Fornecemos o mesmo nível de segurança em todos os dispositivos. Quer seus clientes utilizem um celular, um tablet ou um computador desktop, temos tudo necessário.
Transparente para o cliente
Proteja seus clientes de forma passiva.
Ao analisar informações comportamentais e baseadas em dispositivos, proteja seus usuários enquanto eles utilizam seu ambiente. Sem nenhum problema.
Reconheça seus usuários bons
Com nossa precisão de mais de 99%, evitamos falsas recusas e problemas desnecessários.
Reduza os problemas e trate seus clientes bons com a confiança que eles merecem. Deixe os problemas apenas para o tráfego de alto risco.
Menos revisões manuais
Alivie sua equipe de combate à fraude.
O elevado nível de precisão e a poderosa ferramenta de análise permitem à sua equipe de combate à fraude concentrar-se nos casos mais críticos e descobrir novos padrões de fraude.
Para que a autenticação baseada em risco é usada?
Identidade do cliente
Proteja as contas e transações dos clientes contra atividades fraudulentas.
Identidades de terceiros
Gerencie os riscos associados a parceiros externos, vendedores e provedores, implementando medidas de autenticação adaptáveis.
Identidades de funcionários
Assegure o acesso seguro a recursos e dados confidenciais da empresa, atenuando as ameaças internas e o acesso não autorizado.


Thales considerada líder global
Encontre o produto ou serviço que melhor satisfaz suas necessidades e saiba por que a KuppingerCole considera a Thales como líder de mercado, líder global e líder em inovação em gerenciamento de acesso
Recursos recomendados
Perguntas frequentes
As soluções RBA são desenvolvidas com a conformidade em mente, aderindo aos regulamentos do setor, como PSD2, GDPR, PCI DSS, HIPAA, entre outros. Ao incorporar as melhores práticas e ao manter-se atualizada com as alterações regulamentares, a RBA ajuda as empresas a manter a conformidade e a melhorar a segurança.
Sim, as soluções RBA são altamente personalizáveis para se alinharem com a tolerância ao risco, os requisitos de conformidade e os fluxos de trabalho exclusivos da sua empresa. É possível adaptar critérios de avaliação de riscos, definir limites e integrar a RBA sem problema na sua infraestrutura de gerenciamento de identidade e acesso (IAM) existente.
Sim. Nossas soluções de identidade baseiam-se em uma estrutura modular em que os aplicativos individuais (funcionalidades) podem ser adquiridos separadamente.