Accelerate Transformation of Existing Sensitive Data
Protect sensitive information in database columns quickly and efficiently using encryption or tokenization with minimal disruption, effort and cost.
Refresh Cryptographic Keys Efficiently
Avoid taking your systems offline by rotating your database encryption keys in the background to ensure compliance with data protection regulations does not become a burden that affects your system availability.
Reduce Risk when Sharing Data
Leverage static data masking to remove the sensitive information before sharing with third-party developers and big data environments while maintaining your data integrity but still supporting the critical testing and analytical activities.
Efficient Encryption
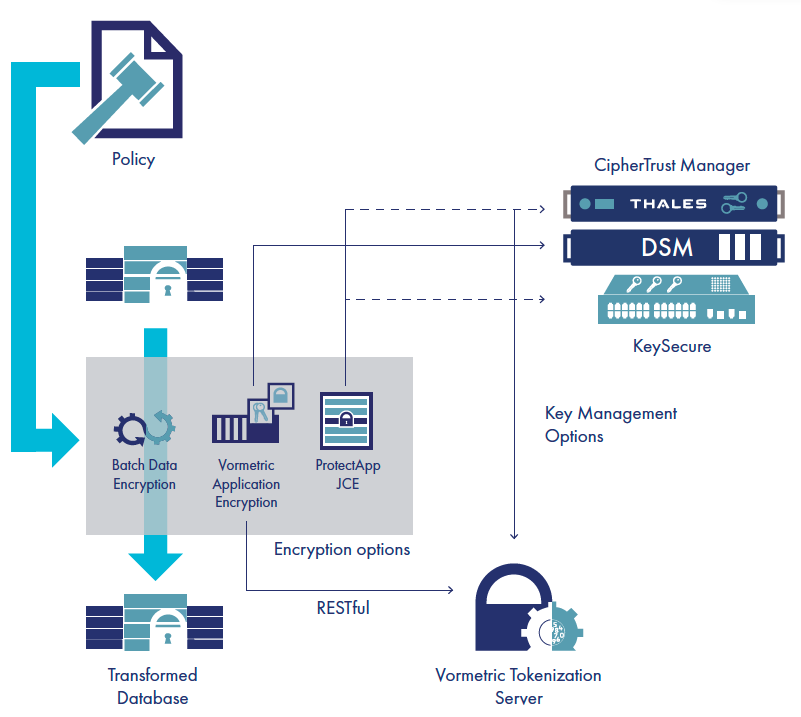
High volumes of data can be encrypted quickly by using the Batch Data Transformation utility in conjunction with Vormetric Application Encryption. Associated policy files can be configured to define encryption options including standard AES encryption or format preserving encryption, while identifying the database columns to be protected and the number of records in the batch.
Flexible Tokenization
As an alternative to encryption, the utility can be used in conjunction with the Vormetric Tokenization Server to tokenize selected columns in the database using a policy-based approach for the number of records specified in the batch. This avoids the need for any application changes and helps ensure that sensitive information such as credit card numbers are not stored in the clear. The reverse de-tokenize process is supported so that your applications can access the clear data again when required.
Static Data Masking
In situations where sharing a representative database with a third party is required, sensitive data needs to be removed in advance because of compliance and security concerns. Static data masking is an effective method supported by the Batch Data Transformation utility that keeps the data accurate, consistent and safe. It even supports tokenizing dates within your defined date range.
Data transformation options:
- Format Preserving Encryption (FPE) with ASCII and Unicode character set options
- Cipher Block Chaining using the AES-CBC-PAD encryption mode
- Format preserving alpha/numeric
Configuration file options:
- Data encryption parameters
- Data tokenization parameters
- Number of process threads for the data transformation process
- Data batch size (number of records to be transformed)
- TLS configuration settings to support secure communications
- Input, output and log file locations (.csv file format)
- Password control
Policy file options:
- Specific action for each individual column transformation – encrypt, decrypt, tokenize, de-tokenize and re-key
- Easy to apply retrospective encryption without the need for application changes
- Flexible key management options – keys in HSM or server, multiple key support
Hardware and Operating System requirements:
- Processor with 4 cores, 16GB RAM (minimum)
- Java Runtime Environment (JRE)
- Windows
- Linux – RedHat, CentOS, Ubuntu and SUSE