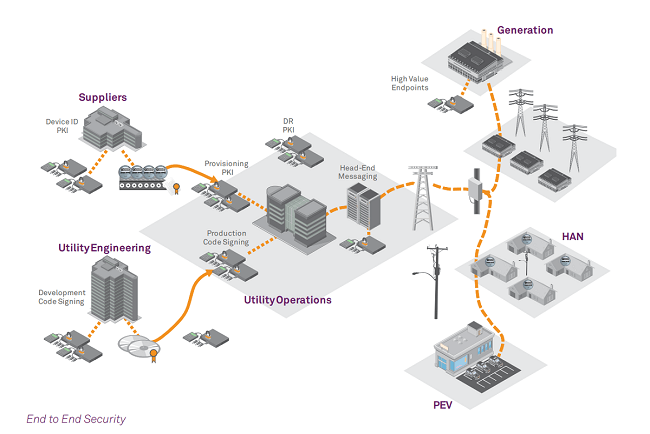
At a time where energy utilities play an increasingly important part of our everyday lives, smart grid technologies, including those leveraging the Internet of Things (IoT), introduce new smart grid security challenges that must be addressed.
Implementing a smart grid without proper advanced metering infrastructure (AMI) security could result in grid instability, loss of private information, utility fraud and unauthorised access to energy consumption data. Without the proper security, the benefits of IoT-based energy such as trusted by-directional communication between applications and devices, as well as secure collection of information for accurate big data analytics, would not be realised. Effective security arms manufacturers, consumers and utility providers with the confidence to leverage the power of the IoT.
Building a trusted, secure smart grid will require robust smart grid security solutions that can be easily deployed at the communication and application layers of the smart grid infrastructure.