Transparent data protection
Transparent and continuous file-level encryption that protects against unauthorised access by users and processes in physical, virtual and cloud environments. Transparent file encryption implementation is seamless and fast, keeping both business and operational processes working without changes even during deployment and roll out.
Scalable and easy to deploy
Scaling to deployments of tens of thousands of physical or virtual servers, the Vormetric transparent encryption solution is available for Windows, Linux and Unix platforms. The enterprise encryption software can be used, deployed and maintained across physical, cloud, container and big data environments.
Meet compliance and best practice requirements
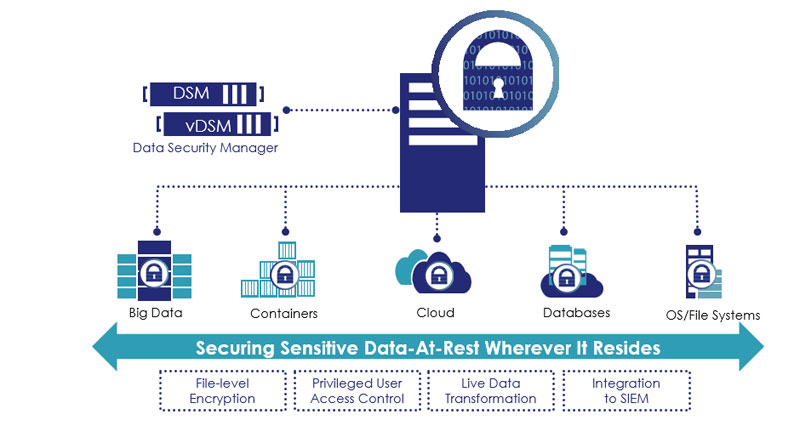
Encryption, access controls and data access logging are basic requirements or recommended best practices for almost all compliance and data privacy standards and mandates, including PCI DSS, HIPAA/Hitech, GDPR and many others.
Define Granular Access Controls
Role-based access policies control who, what, where, when and how data can be accessed. Access controls are available for system level users and groups as well as LDAP, Active Directory, Hadoop and Container users and groups. Easily implement privileged user access controls to enable administrators to work as usual, but protect against users and groups that are potential threats to data
High-performance hardware accelerated encryption
Vormetric transparent encryption only employs strong, standard-based encryption protocols, such as the Advanced Encryption Standard (AES) for data encryption and elliptic curve cryptography (ECC) for key exchange. The agent is FIPS 140-2 Level 1 validated. The overhead from encryption is minimised using the encryption capabilities available in modern CPUs. A distributed agent-based deployment model eliminates the bottlenecks and latency that plague legacy proxy-based encryption solutions.
Broadest Operating System and Environment Support
Secure structured databases and unstructured files across data centres, cloud, containers and big data environments on Linux, Windows and Unix with a single infrastructure and management environment. Encryption, access control and data access audit logging are available without changes to infrastructure, applications or workflow for maximum control with minimal costs and resource requirements.
Comprehensive security intelligence.
Identify and stop threats faster with detailed data access audit logs that not only satisfy compliance and forensic reporting requirements, but also enable data security analytics. Pre-built integration and dashboards that make it easy to find denied-access attempts to protected data are available for major system vendors.
Zero-Downtime Data Transformation
Eliminate the downtime required for initial encryption operations by adding the Live Data Transformation option. This patented technology allows for databases or files to be encrypted or re-keyed with a new encryption key while the data is in use without taking applications offline. There is no other data encryption solution that offers this unique capability.
Platform support:
Microsoft—Windows Server 2019, 2016 and 2012; Linux—Red Hat Enterprise Linux (RHEL), SuSE Linux Enterprise Server, AWS Linux and Ubuntu; UNIX—IBM AIX.
Database support:
IBM DB2, MySQL, NoSQL, Oracle, SQL Server, Sybase and others
Application support:
Transparent to all applications, including Microsoft, Documentum, SAP, SharePoint, custom applications, and more
Big data support:
Hadoop – Cloudera, Hortonworks, IBM; NoSQL – Couchbase, DataStax, MongoDB; SAP HANA; Teradata
Encryption hardware acceleration:
AMD and Intel AES-NI, IBM P9 cryptographic coprocessor
Agent certification:
FIPS 140-2 Level 1
Container support:
Docker, OpenShift
Cloud storage support:
AWS: EBS, EFS, S3, S3I, S3 Glacier
AZURE: Disk Storage, Azure Files