Identidade do cliente
Capacite seus clientes com experiências de cliente perfeitas, seguras e conformes
Saiba maisA partir do momento em que interagimos com uma plataforma ou serviço, nossa identidade molda a experiência: a forma como somos reconhecidos, o nível de personalização que recebemos e a confiança que depositamos na interação. É por isso que a Thales está empenhada em fornecer tudo o que é necessário para gerir identidades com sucesso.
As soluções de gerenciamento de identidade e acesso da Thales garantem que os indivíduos certos têm acesso aos recursos certos, nos momentos certos e pelas razões certas. Estamos aqui para fornecer a experiência, as capacidades e o suporte necessários para tornar os processos de IAM simples, fáceis e mais confiáveis.
A Thales orgulha-se de ter sido nomeada vencedora na categoria Identity Trailblazer no Microsoft Security Excellence Awards 2024, em reconhecimento das nossas soluções inovadoras de IAM.

Capacite seus clientes com experiências de cliente perfeitas, seguras e conformes
Saiba mais
Modernize a colaboração entre parceiros. Crie experiências de confiança com soluções IAM adaptadas às relações externas
Saiba mais
Onboarding e offboarding do colaborador independente com facilidade e segurança
Saiba mais
Aumente a produtividade e a eficiência, garantindo que os funcionários têm acesso seguro e eficiente a aplicativos
Saiba maisA Thales oferece soluções de gerenciamento de identidade e acesso concebidas para gerir e autenticar de forma segura identidades de pessoas que acessam serviços digitais. Nosso pessoal e nossas tecnologias fornecem às empresas os recursos necessários para melhorar a experiências do usuário, aumentar a confiança dos clientes e modernizar a administração de identidades.
Melhore a comodidade do usuário com um login e uma criação de conta sem problema. Fortaleça a segurança e garanta a conformidade com métodos de autenticação adicionais ou progressivos.
Permita que o usuário transfira sem problema sua identidade de uma plataforma para outra.
Proteja seus clientes contra o acesso não autorizado com camadas adicionais de segurança.
Comprove e valide as identidades dos seus clientes online com os requisitos KYC.
Melhore a segurança e cumpra requisitos regulamentares com chaves de acesso e medidas de autenticação fortes.
Minimize os riscos de fraude com capacidades de autenticação adaptáveis.
Permita que seus clientes eliminem senhas e viabilize o engajamento com sua marca.
Assegure que apenas os usuários legítimos tenha, acesso aos serviços bancários digitais.
Planeje a jornada do cliente com personalização e conformidade em primeiro plano. Crie um perfil de cliente completo de uma forma não invasiva. Fortaleça a confiança e a lealdade do cliente mostrando seu empenho em proteger sua privacidade e o seu espaço digital.
Otimize o envolvimento, personalize as interações e impulsione as conversões com uma jornada de usuário customizada.
Fortaleça a confiança de seus clientes e garanta a conformidade com processos transparentes de gestão de consentimento.
Crie um perfil de cliente completo através da coleta gradual e eficaz de dados eficaz, sem causar incômodo.
Simplifique o controle de acesso, aplique políticas de autorização consistentes e fortaleça a segurança da API para impulsionar o crescimento digital contínuo.
Simplifique o controle de acesso e atribua e gerencie facilmente funções aos usuários.
Estabeleça políticas de autorização consistentes e permita o controle de acesso com base nos atributos do usuário.
Aplique políticas de acesso adaptáveis a pessoas, grupo ou aplicativo com diversas opções de autenticação.
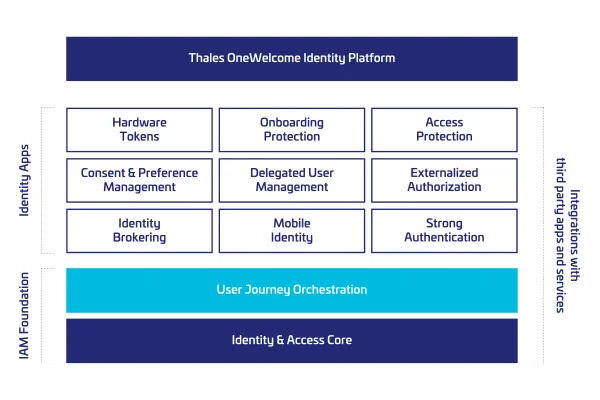
A plataforma de identidade OneWelcome capacita as empresas com um conjunto versátil de aplicativos de identidade adequados a uma vasta gama de casos de uso, incluindo identidades de clientes, parceiros e provedores. Os aplicativos de identidade podem ser misturados e combinados para ajudar a atingir seus objetivos de IAM rapidamente e com menos complexidade.
A plataforma suporta vários métodos de autenticação FIDO2 passkeys, tokens de hardware, cartões inteligentes e autenticadores de software, garantindo o acesso seguro em diferentes ambientes e dispositivos.
Os autenticadores da Thales abordam vários casos de uso, níveis de garantia e vetores de ameaça usando protocolos atuais e emergentes (OTP, PKI, FIDO), bem como de vários fatores de forma (cartões inteligentes e tokens virtuais e de hardware, autenticadores de software e móveis).
O SafeNet Trusted Access, nosso serviço IAM em nuvem para a força de trabalho ajuda a criar jornadas de autenticação intuitivas e seguras. Acelere a transformação para a nuvem, proteja infraestruturas híbridas, reduza o risco de TI shadow e facilite o trabalho.
O SafeNet Authentication Service Private Cloud Edition (SAS PCE) é uma plataforma de autenticação no local que torna a autenticação fácil e econômica de implementar e gerir. Nossa abordagem consistiu em conceber uma solução que elimina muitos dos pontos problemáticos tradicionais da autenticação.
A Thales ajuda os bancos aproveitar sua transformação digital em curso, garantindo a confiança dos clientes e a conformidade regulamentar. O IdCloud, agora parte da plataforma de identidade OneWelcome, é um conjunto de serviços geridos em nuvem que permite às instituições financeiras combinar a prova de identidade, a autenticação forte do cliente (SCA) e a gestão de riscos para garantir a integração e o acesso aos serviços bancários digitais.