- Simple one-click application delivers advanced protection with minimal effort.
- Apply protection without accessing or modifying the original application source code.
- Compatible with a wide range of platforms and environments.

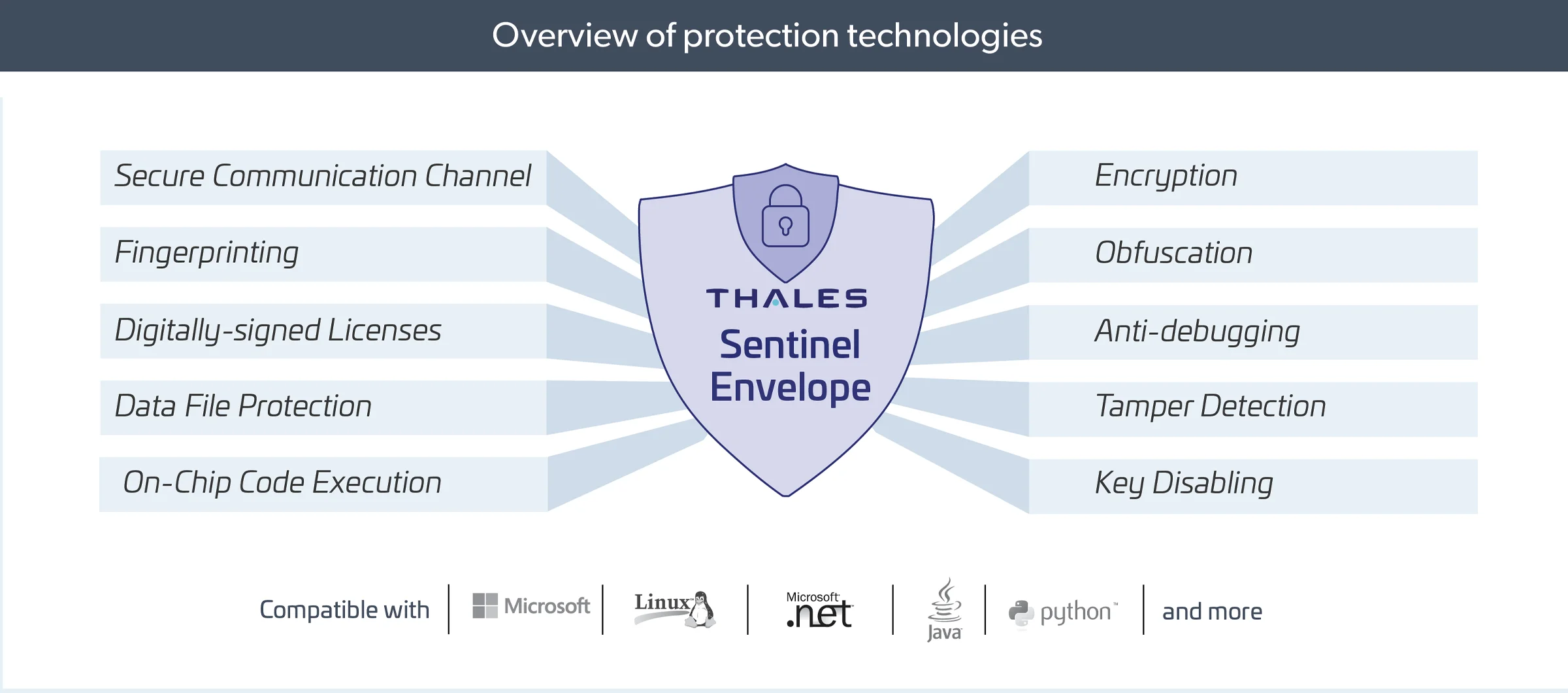
Sentinel Envelope is an automatic file packer with advanced security capabilities. It works together with licensing keys to protect your product from reverse engineering, tampering, piracy, and counterfeit licensing.
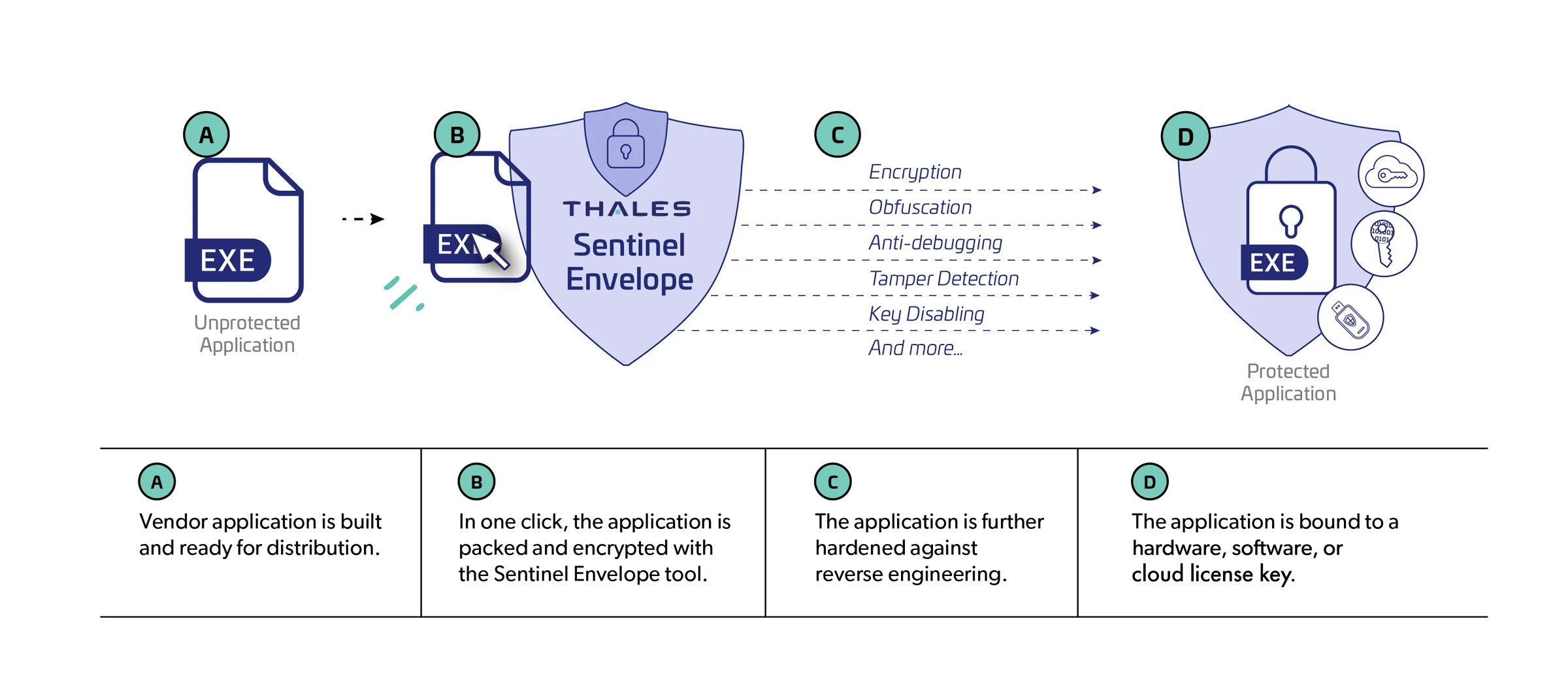
Envelope Capabilities:
Encryption of Code, Data, and Files
- Using technologies such as executable and library encryption, method- and class-level encryption.
- All components encrypt the compiled code using state-of-the-art technologies to achieve maximum protection.
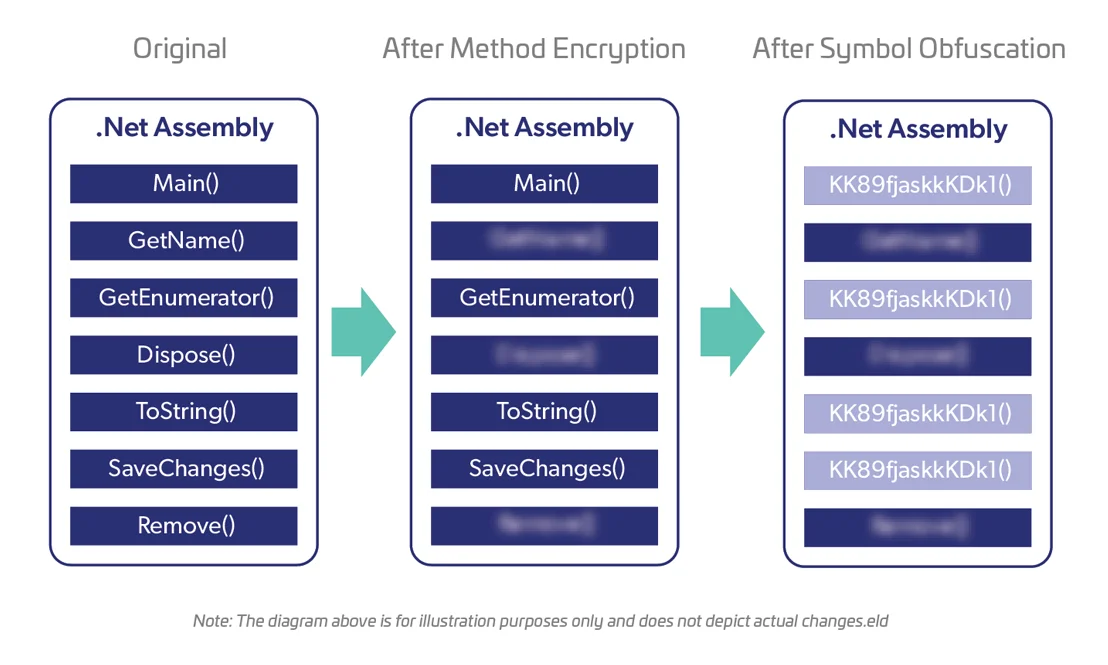
Code and Symbol Obfuscation
- Applicable to .net and Java.
- Code and symbols are obfuscated making analysis and reverse engineering more difficult.
Key Disabling
- Attackers cannot proceed with reverse engineering because the license key (which is essential for the application to run) is disabled as soon the cracking attempt is detected.
- Only the vendor can re-enable the license.
Anti-Debugging & Anti-Tracing
- Continuous monitoring for active debuggers, stops the application from running if malicious elements or tampering are detected.
Quiz Master Technology
- Innovative security model that ensures the encryption engines have not been tampered with. Introduces randomized runtime values to further thwart crackers.
Integrity Checks
- Checks to ensure the entire binary (code and resources) were not modified by checking that the protected application is signed with a digital signature.
Distinct Data Files Protection
- In addition to protecting executables, Sentinel Envelope protects data files.
- Encrypting data files protects valuable content against unauthorized use.
- Data protection utility pre-encrypts files and prepares them for decryption by the Envelope-protected application.
- You can require a dedicated license for data file decryption, or data files can share the same license as the application.
- This feature is used to separate data files from application code, enabling differentiated monetization of content or other file-sourced resources.
Seamless Integration
- Ensures a cracker can’t split between the original application and the protected code because there is no clear seam where the original code ends and the protected code starts.
Envelope provides comprehensive software protection for vendors across all industries. Managed code frameworks and scripts, AI Models, and highly sensitive functions are just a few examples of the specialized protection scenarios we support. If you have a unique requirement, we can help. Contact us today.
Protecting Managed Code Frameworks and Scripts
- .NET, Java, and Python executables are inherently more exposed than native code. Dedicated technologies protect these higher-risk environments with specialized protection techniques.
Use Cases: Enterprise Applications, Web Application, Cloud Applications, Machine Learning Applications
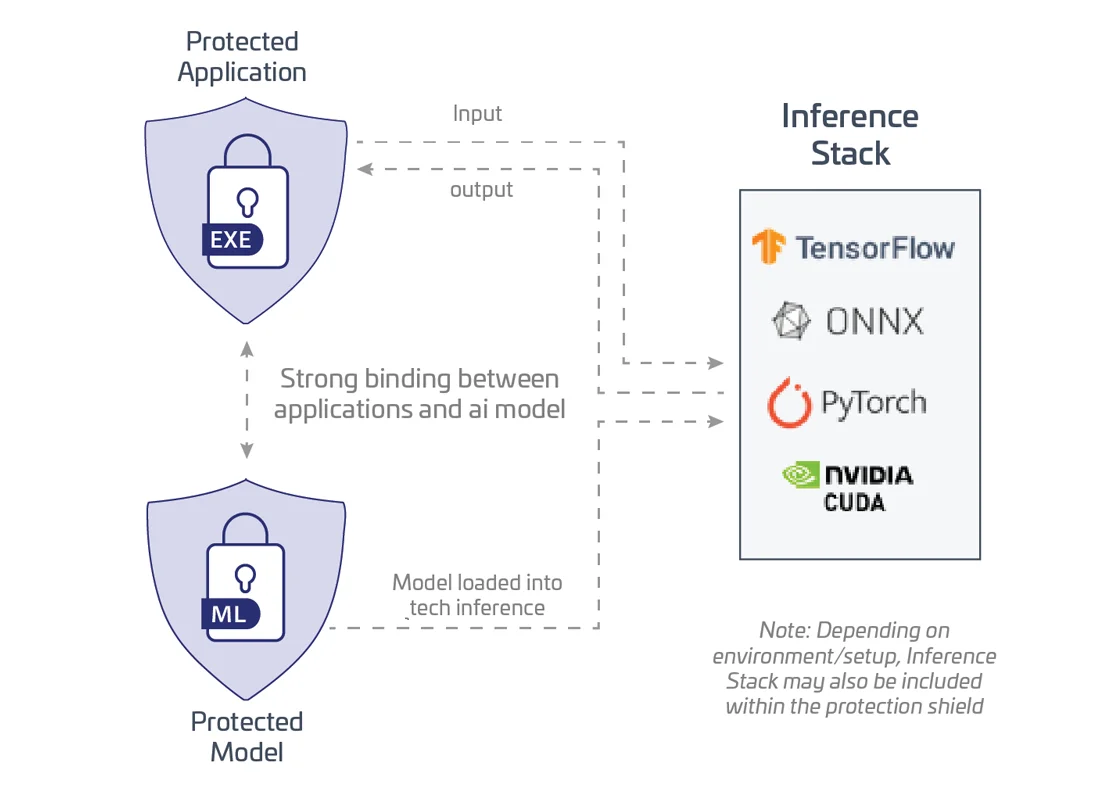
Protecting AI
- Sentinel protects both the application and the model file.
- Protected application – Protects application code from disassembly and reverse engineering. Coupled software piracy protection.
- Encrypted model file – Protects model from adverse modifications by preventing targeted changes to parameters, weights, and biases.
Use Cases: Protecting LLMs, Protecting GenAI, Protecting AI enabled features within on-premises applications, e.g. healthcare and medical devices, supply chain and manufacturing, and customer insights
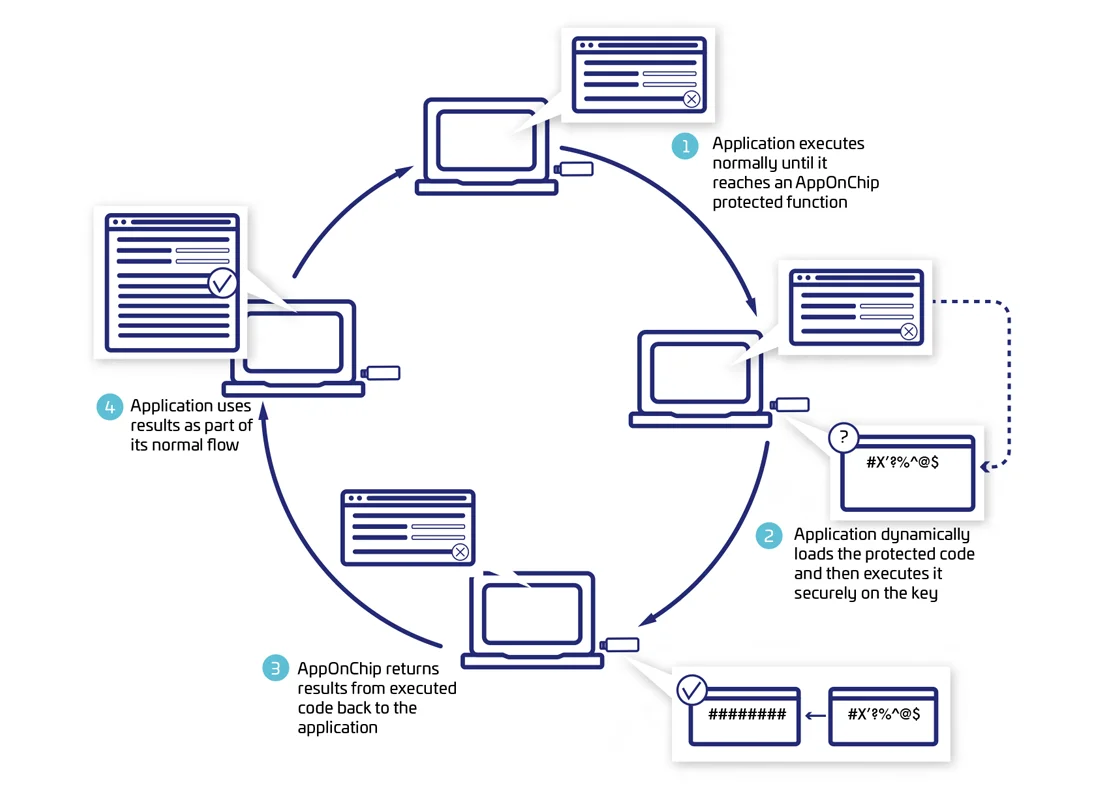
Maximum Protection with On-Chip Code Execution
- Envelope extracts the code, converts it into an executable format supported by the hardware chip, encrypts it, and embeds it in the binary, replacing the original code.
- At runtime, the protected application uploads the encrypted code to the hardware key where it is decrypted and executed securely, out of reach of cracker tools like debuggers.
Use Cases: Providers with stringent security requirements, vendors that can/want to distribute software with dongles.