Full Suite of Crypto Functions
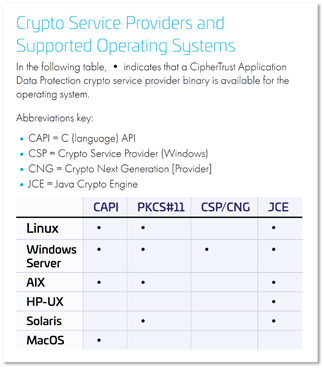
With comprehensive Crypto Service Providers (CSP) reflecting both industry standard PKCS#11 and KMIP as well as support for Java Crypto Engine, (JCE) Microsoft Crypto Service Provider (CSP) and Crypto Next Generation (CNG), developers and security administrators can select the crypto services, similar to HSM services, that best fulfill the complex needs of the modern organisation. Core crypto functions include encryption/decryption, sign, hash (SHA) and HMAC. For convenient data protection avoiding the need for in-application key management, consider CipherTrust Tokenisation.
Wealth of Encryption Algorithms
Encryption algorithms and corresponding keys include 3DES, AES 256 (CBC and XTS), SHA 256, SHA 384, SHA 512, RSA 1024, RSA 2048, RSA 3072, RSA 4096, and ECC as well as format preserving FF1 and FF3.
Automated Key Rotation
Built-in, automated key rotation for all crypto functions except for hash.
Many Deployment Choices
- Applications linked with the development libraries are installed on each application server
- Local crypto operations offer the lowest latency and potentially highest performance. Keys are encrypted when not in use and obfuscated in memory when in use
- Crypto operations may be directed to CipherTrust Manager clusters. This choice keeps keys in the key source for the highest key security.
- A lightweight deployment option is to install the encryption and key management libraries on a web server and access them from an application server using SOAP or REST APIs
- The lightest deployment option is to access crypto functions using a RESTful API fulfilled directly by CipherTrust Manager clusters
Rich Ecosystem of Solutions
Key management and/or encryption services is available for a formidable ecosystem of solutions including Linux Unified Key Setup (LUKS) and key management for Transparent Data Encryption (TDE) vendors including Oracle, Microsoft SQL Server, and HashiCorp Vault, among many others.

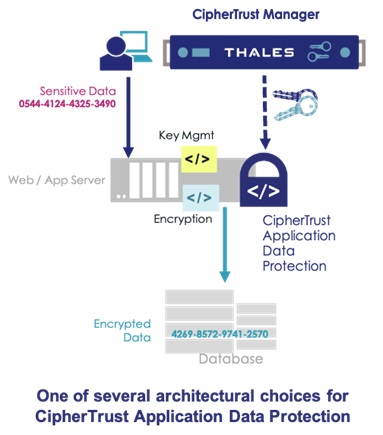 CipherTrust Application Data Protection delivers on the promise of DevSecOps. Developers enjoy language bindings appropriate to their projects. Operations can leverage choices among Crypto Service Providers that run on a wide range of operating systems. The product includes many operational features that enhance performance and availability to ensure that security imposes a minimal to zero impact on business operations. And for the security team, it operates with
CipherTrust Application Data Protection delivers on the promise of DevSecOps. Developers enjoy language bindings appropriate to their projects. Operations can leverage choices among Crypto Service Providers that run on a wide range of operating systems. The product includes many operational features that enhance performance and availability to ensure that security imposes a minimal to zero impact on business operations. And for the security team, it operates with 

