CipherTrust Data Security Platform
Discover, protect and control your organisation’s sensitive data anywhere
with next-generation unified data protection.
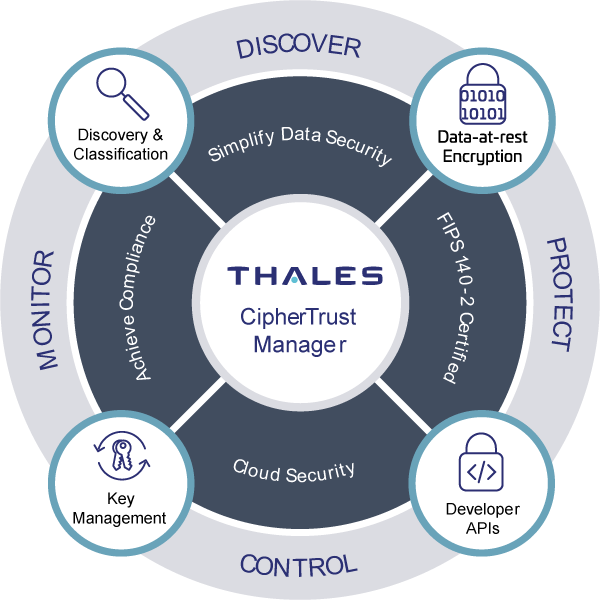
Thales has pushed the innovation envelope with the CipherTrust Data Security Platform to remove complexity from data security, accelerate time to compliance, and secure cloud migrations. This next-generation platform is built on a modern micro-services architecture, is designed for the cloud, includes Data Discovery and Classification and fuses together the best capabilities from the Vormetric data security platform and KeySecure and connector products. CipherTrust data security platform unifies data discovery, classification, data protection and unprecedented granular access controls with centralised key management – all on a single platform. This results in fewer resources dedicated to data security operations, ubiquitous compliance controls and significantly reduced risk across your business.
The CipherTrust Data Security Platform is an integrated suite of data-centric security products and solutions that unify data discovery, protection and control in a single platform.
Cost Savings and Business Benefits
Enabled by the CipherTrust Data Security Platform

A free-forever version of the CipherTrust Data Security Platform that makes it easy for DevSecOps to deploy data protection controls into hybrid and multi-cloud applications – in minutes instead of weeks. It supports the following DevSecOps use-cases.
Simplify Data Security
Discover, protect and control your organisation’s most sensitive data on-premises and in the cloud on an integrated data security platform.
Accelerate Time to Compliance
Comprehensive data security capabilities, including data discovery and classification, encryption, granular access controls, audit logs, tokenisation and key management support ubiquitous data security and privacy requirements.
Secure Cloud Migration
Confidently move workloads to the cloud and hosted environments and repatriate data back on-premises, knowing that your data remains in your control.
Data discovery and classification
Data protection techniques
Centralised enterprise key management
Monitoring and reporting

451 Research examines Thales’s next-generation data protection platform to discover, protect and control sensitive data on a single platform.Uniting KeySecure and Vormetric product lines, CipherTrust Data Security Platform combines the strengths of both encryption and key...
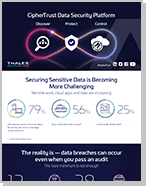
Remote work, cloud apps and data are increasing Key Points/Stats from this Infographic: 79% of businesses remain concerned about the security risks of an increasingly remote workforce 56% know where their data is stored 25% could classify all their data

Traditionally organizations have focused IT security primarily on perimeter defense, building walls to block external threats from entering the network. However, with today’s proliferation of data, evolving global and regional privacy regulations, growth of cloud adoption, and...

As data breaches continue at alarming rates, securing sensitive data is critical to all organizations. In addition, organizations struggle to stay compliant with evolving global and regional privacy regulations, and securing the cloud in the face of accelerated adoption...

Thales has pushed the innovation envelope with the new CipherTrust Data Security Platform that unifies data discovery, classification, and data protection. It enables organizations to remove data security complexity, accelerate time to compliance, and secure cloud migrations....

To meet the scale of current and future data security threats, evolving global and regional privacy regulations, and cloud adoption brought on by remote working, organizations need an easier and unified approach to discover, protect and control their sensitive data.Thales has...

The CipherTrust Data Security Platform (CDSP) increases data security, accelerates time to compliance, and secures cloud migration – which decreases resources required for data security operations. You can discover, protect and control your organization’s sensitive data to...

CipherTrust Platform Community Edition is a free-forever version of the CipherTrust Data Security Platform that makes it easy for DevSecOps to deploy data protection controls into hybrid and multi-cloud applications. It includes CipherTrust Manager Community Edition and...

Discover the contents of this report as KuppingerCole rates all the market leaders in database and big data security solutions. With the average cost of a data breach reaching $4 million, companies face financial and reputational damages as well. High-profile “mega...
The CipherTrust data security platform integrates data discovery, classification, data protection and unprecedented granular access controls, all with centralised key management. Watch the demonstration of CipherTrust data security platform in action.
CipherTrust Manager is the central management point for the CipherTrust data security platform. Offers an industry-leading enterprise key management solution to centrally manage encryption keys and configure security policies.
Enables organisations to get complete visibility into sensitive data with efficient data discovery, classification and risk analysis.
Delivers high-performance encryption and least-privileged access controls for files, directories and volumes.
Transparently protect data accessible from containers and containerised applications.
Delivers crypto functions such as key management, signing, hashing and encryption services through APIs.
Transparently protect sensitive data in RESTful calls.
Quickly add tokenisation and dynamic data masking to existing applications to protect data and meet regulations.
Delivers comprehensive encryption and granular controls to secure the most sensitive data across your database environments.
Transform data fast and easily for bulk encryption, initiate database tokenisation and create desensitised databases with static data masking.
CTE Ransomware Protection protects businesses against ransomware and unauthorised ransomware encryption by continuously monitoring processes for abnormal I/O activity.
Enables organisations to establish strong controls over encryption keys and policies for data encrypted by multiple cloud providers.
Supports a broad range of KMIP compatible devices and environments to comply with compliance standards and best practices with centralised encryption key management.
Provides lifecycle management for Oracle TDE Master Encryption Keys and Microsoft SQL Server database encryption keys to meet compliance and best practice requirements.