Sentinel License Development Kit (LDK)
Protect your software with easy to use licensing
LDK is an easy-to-implement solution that puts you in control of how your customers use your software. Using the powerful licensing and entitlement solutions in LDK, you can implement flexible business models, become more customer-centric, and protect your IP.
Sentinel LDK is a fully loaded software development kit that helps you efficiently manage your software licensing and entitlements. After implementing LDK you'll be able to streamline the way you issue, track, and monitor licenses to ensure you are getting the best value from your customers.



Discover strategies for building predictable revenue and sustainable growth with Thales' guide to transforming your business with recurring revenue.

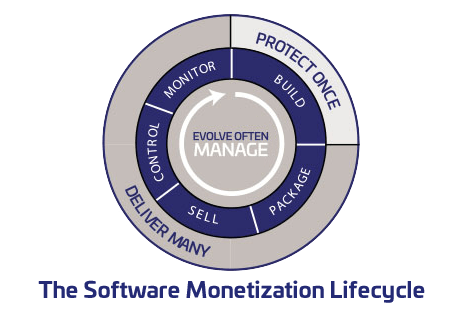
A comprehensive, out-of-the-box software monetization solution that enables you to protect your software, maximize revenues and simplify operational processes.

€14 M
€700,000
€5 M



Delivering physical goods can be a challenge such as hardware keys. Having IT departments wait 2-3 days to get a security key can be troublesome. Accessing office networks during a pandemic can be unreliable.
Cloud licensing has many advantages such as one identity of user, only one license will work at a time if they have installed on many machines which helps eliminate the need to activate the license on multiple devices; and thus helps eliminate piracy. It is also more secure and reliable.
For Independent software providers (ISVS), it also eliminates the need for shipping physical keys.
For Customers: Using the product reliably when accessing their office network is a challenge, this helps eliminate the need to collect physical keys.
LDK with EMS: Can sell the cloud service along with EMS so it reduces the need for IT departments to maintain servers or to get to the office. Being able to grand licenses through the cloud allows the product to be easier to use, consume, and be more reliable with this model of licensing.
Cost Reduction, and increased efficiency, easy deployment in Linux, Windows, Mac, and cloud support. Consumes licenses anywhere, deploy them AWS, GCP, Azure, On Premise. Services for new and existing customers, replaces the vast IT efforts of ISVS
Always updated, so security is always high
The container, Run all machines
Benefits of using Docker: