Automatically strengthen security while streamlining user experience
Traditional authentication methods are inadequate against the rising cyber threat landscape. Automated and increasingly sophisticated attacks mimic human behavior to outsmart standard bot-detection tools. Risk-based authentication (RBA) systems are finely tuned to detect fraudulent behavior, dynamically evaluating and responding to the risk level of each login attempt. Strengthen your defenses by integrating a series of authentication techniques and behavioral biometrics and introduce the appropriate level of assurance in every authentication journey.

Enhance Security
Stop evolving threats and adapt security measures based on the perceived level of risk

Improve User Experience
Dynamically adjust authentication requirements without unnecessary interruptions

Comply with regulations
RBA has become an essential solution to safeguard customers, especially in heavily regulated industries like banking
Banking in the cloud: Why Risk Based Authentication is Vital for Financial Institutions
As more consumers turn to digital banking, they expect to be able to onboard and access financial institutions (FIs) with ease using RBA.

Balance security and convenience
Enhance the user experience and security, and optimise fraud detection with the IdCloud risk management solution.
HOW THALES CAN HELP
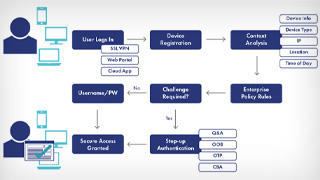
What is Risk-based Authentication?
Risk-based authentication (RBA) is an intelligent identification approach that evaluates various factors, such as user behavior, device characteristics, and environmental context, to determine the risk level of a login attempt. It automatically undertakes a risk assessment of a customer and determines threat risk based on those characteristics – including a user’s IP address, physical location, browser history, etc. This proactive authentication method allows organisations to adapt their security measures based on the perceived risk.
How does Risk-based authentication work?
By integrating our risk-based authentication solution into your authentication journey, the risk level of each customer transaction is analysed. Recommendations for the most suitable authentication method are then automatically provided, reducing account takeover (ATO) fraud. With risk-based authentication, continuously adaptive policies based on customer segmentation, preferences, and use cases can be defined. These RBA authentication capabilities operate quietly in the background to ensure the best end-user experience.
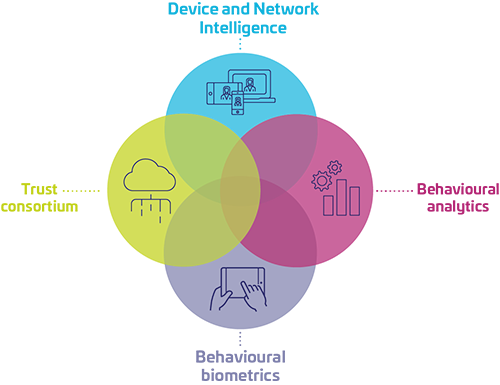
Benefits of RBA for enterprises and end-users
Real-Time Detection
Find anomalous activity before it results in fraud.
With our real-time solution, threats get blocked as they try to access your environment.
Customised Security
Your traffic, your rules.
We help you secure your environment on your own terms. Automate the actions you want based on your user's risk levels and risk thresholds.
Multi-Channel Security
Have all devices under control.
We provide the same level of security on every device. Whether your customers are using mobile, tablet or desktop we've got them covered.
Transparent to the Customer
Protect your customers passively.
By looking at behavioral and device-based information, protect your users while they seamlessly enjoy your environment. No friction added.
Recognise your good users
With our +99% accuracy, you avoid false declines and unnecessary friction.
Reduce friction and treat your good customers with the trust they deserve. Leave friction for high-risk traffic only.
Less Manual Reviews
Relieve your fraud team.
High level of accuracy and powerful analyses tool allows your fraud team to focus on the most critical cases and uncover new fraud patterns.
Who is Risk-based authentication used for?
Customer Identities
Safeguard customer accounts and transactions from fraudulent activities.
Third-Party Identities
Manage risks associated with external partners, vendors, and suppliers by implementing adaptive authentication measures.
Workforce Identities
Ensure secure access to sensitive company resources and data, mitigating insider threats and unauthorized access.


Thales Named an Overall Leader
Find the product or service that best meets your needs, and learn why KuppingerCole named Thales a Market Leader, Overall Leader, and Innovation Leader in Access Management
Recommended resources
Frequently asked questions
RBA solutions are developed with compliance in mind, adhering to industry regulations such as PSD2, GDPR, PCI DSS, HIPAA, and others. By incorporating best practices and staying updated with regulatory changes, RBA helps organisations maintain compliance while enhancing security.
Yes, RBA solutions are highly customisable to align with your organisation's risk tolerance, compliance requirements, and unique workflows. You can tailor risk assessment criteria, define thresholds, and integrate RBA seamlessly into your existing identity and access management (IAM) infrastructure.
Yes. Our identity solutions are based on a modular structure where individual apps (capabilities) can be purchased separately.