Flexible Authorisation for Complex Digital Services
Legacy role-based authorisation systems cannot meet the challenges of effectively and securely managing external and third-party access. This highlights the need for an externalised authorisation architecture, enabling enterprises to decouple business applications from authorization policies and allow them to provide unified, fine-grained authorisations to users across their application landscape.
OneWelcome Identity Platform offers externalised authorisation capabilities that enable you to implement fine-grained, policy-based, centralised access control and enforcement.

Standardised authorisation and consistent security
Centralise permission management on one platform to ensure consistent security policy enforcement across all components.

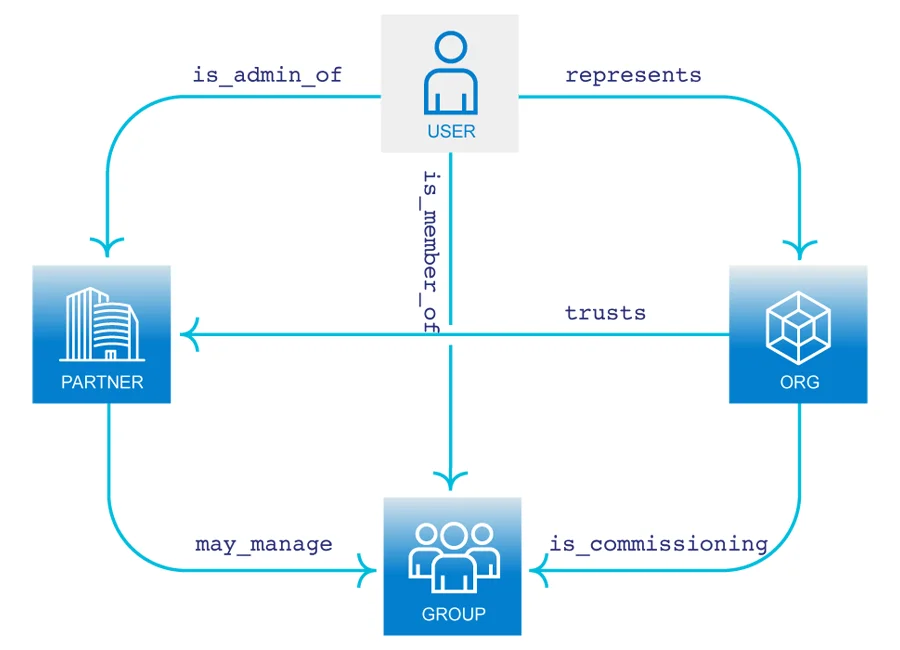
Relationship-based access control
Evaluate relationships between users to determine access

Agile policy management
Separate policy management from the application lifecycle. Reduce complexities and easily edit policies and access requirements in a no-code/low-code setup.
What is Externalised Authorisation?
Externalised authorisation is an application that simplifies the process of defining who has access to what resources and what actions individuals are permitted to perform. It separates policy management and enforcement from the application lifecycle, and delegates access control decisions to a decoupled external decision point. Our OneWelcome Identity Platform offers externalised authorisation capabilities that enable you to implement fine-grained, policy-based, centralised access control that takes relationships and context into account for the access decision.
Which type of identity would you like to protect?
Customer Identities
Create frictionless and secure access for your customers
B2B & Third Party Identities
Streamline access and collaboration across your entire B2B ecosystem
How Externalised Authorisation Works
With centralised access control, you can grant access to your resources in real-time via a centrally managed decision point that leverages user attributes in your identity store and create authorisation policies to determine when to grant users access to your products.
Policies can be graphical or defined in Open Policy Agent’s native query language, Rego. Relationship-based access control (ReBAC) can implement fine-grained access to protected resources based on the user's relationship with other entities.
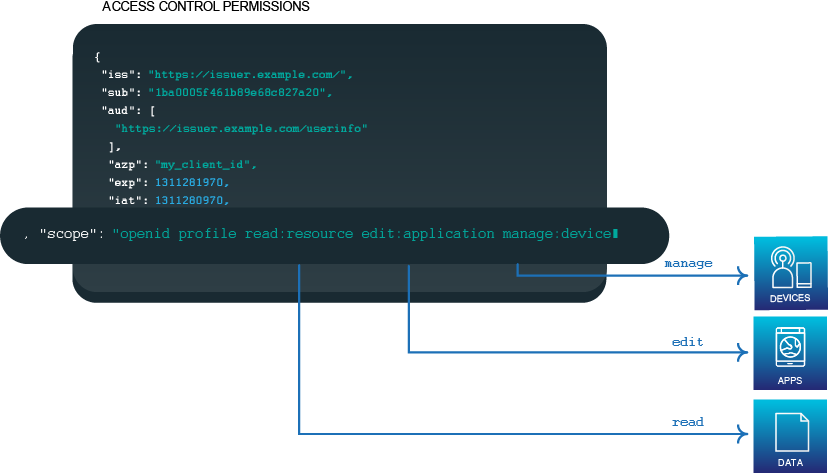
Integration with Thales OneWelcome Identity Platform
Our Externalised Authorisation identity app seamlessly integrates into your existing identity infrastructures. Our customisable design and out-of-the-box capabilities offer you the performance and flexibility to implement state-of-the-art externalised authorisation.


Thales Named an Overall Leader
Find the product or service that best meets your needs, and learn why KuppingerCole named Thales a Market Leader, Overall Leader, and Innovation Leader in Access Management

The relationship between trust and user experience is the foundation of successful online interactions. The imperative is clear: organisations must uphold an unwavering commitment to both data security and user experience to build a future where trust enables digital interactions.
Recommended resources
Frequently asked questions
Use External Authorisation when you need fine-grained control over access permissions, especially in complex environments or when integrating with multiple systems. It's beneficial when you want to centralise authorisation logic, manage permissions externally, or enforce policies across various services.
External Authorisation offers several advantages for simplifying and securing access, including centralised policy management, dynamic policy updates without code changes, support for complex access control scenarios, scalability across distributed systems, and the ability to integrate with multiple identity providers or external sources seamlessly.
Yes, a user can have multiple external identities. The Identity Broker supports federated identities, allowing users to authenticate with various identity providers and consolidating their identities under a single identity record.


