
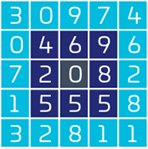
Thales’s GrIDsure flexible authentication method allows an end-user to generate a one-time password without the requirement for hardware tokens or software applications. GrIDsure tokens work by presenting the end-user with a matrix of cells which contain random characters, from which they select a 'personal identification pattern' (PIP).
Whenever a user wishes to authenticate to a protected resource, they are presented with a challenge grid containing random characters. The user then enters the characters in the cells that correspond to their PIP.
The end result is far superior to static passwords. Every time the challenge grid appears, the characters in the cells are different, so the user is always entering a one-time passcode. Plus, there's no hardware to lose.
GrIDsure is supported by SafeNet Trusted Access, and can be used to protect a wide range of use cases, including:
- VPNs
- Network logon
- Cloud applications (Saas)
- Web portals
- VDI
- Specifications
- Features
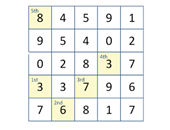 Grid tokens can be customised to optimise the user logon experience and changing security policy.
Grid tokens can be customised to optimise the user logon experience and changing security policy.
Grid sizes offered:
- 5 x 5 cells
- 6 x 6 cells
- 7 x 7 cells
Grid character sets offered:
- Digits
- Upper case letters
- Lower case letters
- Punctuation
- Non-trivial PIPs
Compatible with: Any application supported by SafeNet Trusted Access, including:
- Local network access
- Cloud applications
- VDI
- VPN
- Web portals
 Key features:
Key features:
- Usability: Grid token is easy to use in any user population.
- Zero footprint: There is no hardware to distribute and no client software to install or maintain.
- Ideal for partner and consultant access: GrIDsure is easy to use and to provision, making it ideal for securing external user access. Provision GrIDSure to external partners and contractors to secure access to partner portals or collaboration sites, without the hassle of shipping hardware tokens or installing software tokens.
- Cost effective: This low cost solution becomes even more attractive because there's no administrative overhead with provisioning users with tokens.
Key benefits:
- Pattern based "PIP" are easier to remember than PINs
- Characters in the grid change for each logon
- No software to install or maintain
- No hardware to distribute
- Ideal for protecting web-based applications

Thales GrIDsure Authentication - Product Brief
Providing unparalleled convenience to end users and simple deployment to IT staff, Thales GrIDsure Authentication is Providing unparalleled convenience to end users and simple deployment to IT staff, Thales GrIDsure Authentication is a pattern-based authentication solution...

Industrial Company Triumphs with Flexible Access Security - Case Study
When this industrial enterprise decided to migrate to Microsoft Office 365 in the cloud, they assumed that they were protected. However, they found out the difficult way that only a stronger authentication and access management solution could provide them with more effective...

SafeNet MobilePASS+ Mobile Authenticator App - Push and OTP - Product Brief
End users and IT teams are experiencing waves of high stress due to the pandemic and escalating cyberattacks. Thales offers a simple and highly secure authenticator app that makes login fast and secure throughout each login session, lowering risk and ensuring secure remote...

2020 Access Management Index - US and Brazil Edition - Infographic
Survey of 300 IT professionals across USA and Brazil, shows that overreliance on passwords continues to compromise data security. Discover why Access Management and strong authentication are important in this day and age. Key Points/Stats from this Infographic: ...
