Access Management Risk Assessment Tool
How are you securing your cloud apps? Learn where you are in your cloud adoption journey and how best to secure your apps simply and securely.
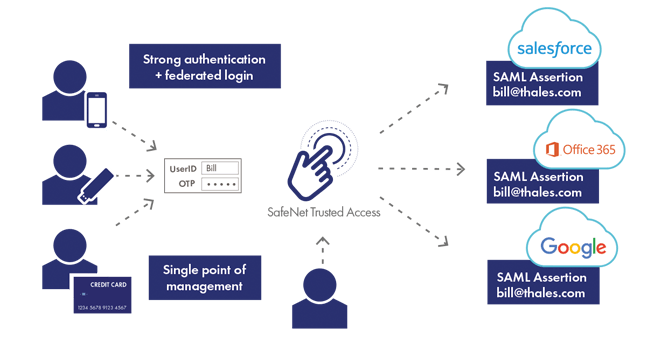
SAML Authentication is a method of identity verification that leverages an identity provider to authenticate users centrally to a broad range of unaffiliated websites. By relaying the authentication process to a single trusted identity provider, organisations realise numerous security, administration and cost savings benefits and above all, relieve users of the need to maintain dozens of different usernames and passwords.
Created by the OASIS non-profit consortium, SAML, or the security assertion markup language, is an open-source XML standard or protocol for exchanging authentication and authorisation information between an identity provider, such as SafeNet Trusted Access, and a relying party or service provider, meaning a cloud or web app, such as such as Office 365, Salesforce, AWS, Zendesk, DropBox etc.
Token-based authentication, security token services, federated authentication and identity federation are all terms that describe the capabilities that a SAML identity provider offers.
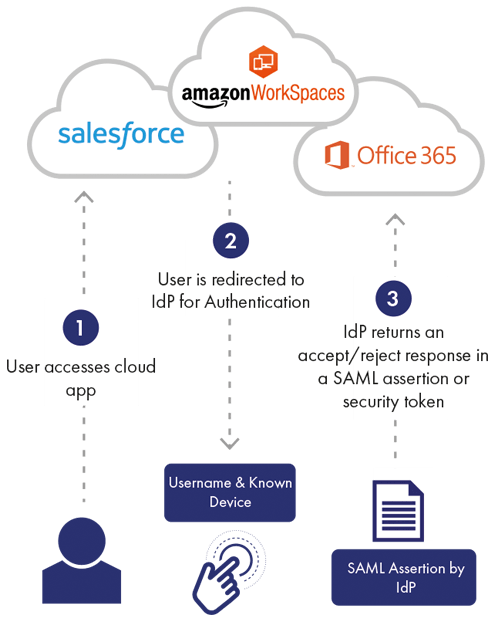
1. With SAML authentication, each time a user accesses an app, the authentication process is relayed to the SAML identity provider.
2. The user enters their credentials (e.g. password, OTP, contextual attributes), which are then verified by the identity provider.
3. The identity provider returns an access or reject response in the form of a SAML assertion. If authentication is successful, the user is granted access to the resource and if not, access is denied.
1. A user accesses an app and is redirected to the identity provider for authentication.
2. They enter their credentials into the login portal.
3. Upon successful authentication, they are logged in to the resource.
 Each cloud and web application works with a different set of SAML attributes, which may include one or more various fields such as user ID, email address, group membership, postal address, alias and others. Therefore, to successfully integrate a central SAML identity provider with a cloud or web app, the identity provider must be able to provide these details in the SAML assertion.
Each cloud and web application works with a different set of SAML attributes, which may include one or more various fields such as user ID, email address, group membership, postal address, alias and others. Therefore, to successfully integrate a central SAML identity provider with a cloud or web app, the identity provider must be able to provide these details in the SAML assertion.
SafeNet Trusted Access makes it a breeze to apply single sign-on using SAML authentication, as it offers a catalogue of pre-integrated applications. Just add the cloud or web app that you already use today and start applying smart single sign-on with business-driven access policies.

How are you securing your cloud apps? Learn where you are in your cloud adoption journey and how best to secure your apps simply and securely.

Organisations are in various stages of moving to the cloud. For those still using AD FS, applying conditional access and the appropriate authentication method is a natural way of applying next generation access management capabilities to their existing environment. Learn how Smart Single Sign-On extends the capabilities of regular federation frameworks and how to benefit from adaptive authentication and conditional access while using AD FS.

Identity and access management key concepts, technologies and standards compiled for you in this Access Management ebook . You will learn: • Authentication and access management differences • How to leverage cloud single sign on (SSO) • Key concepts in Access...

A record number of organisations are moving to Office 365. While offering cloud efficiencies, this move can make organisations more vulnerable to phishing attacks, credential compromise and ultimate data breaches. Learn how to secure O365 at the access point with the appropriate authentication method.