What is a Centralized Key Management System?
As organizations deploy ever-increasing numbers of encryption solutions, they find themselves managing inconsistent policies, different levels of protection, and experience escalating costs. The best way through this maze is often to transition into a centralized encryption key management system. In this key management case, and in contrast to the use of hardware security modules (HSMs), the key management system performs only key management tasks, acting on behalf of other systems that perform cryptographic operations using those keys.
The benefits of a centralized key management system include:
- Unified key management and encryption policies
- System-wide key revocation
- A single point to protect
- Cost reduction through automation
- Consolidated audit information
- A single point for recovery
- Convenient separation of duty
- Key mobility
Related Articles
Secure your data, comply with regulatory and industry standards, and protect your organization’s reputation. Learn how Thales can help.
- Unified Key Management Solutions
- Cracking the Confusion: Encryption and Tokenization for Data Centers, Servers and Applications by Securosis – White Paper
- Thales Key Management – White Paper
- Own and Manage your Encryption Keys – White Paper
- Best Practices for Cloud Data Protection and Key Management – White Paper
- Securing Microsoft Office365 and other Azure applications with CipherTrust Key Broker for Azure – White Paper
- The Importance of KMIP Standard for Centralized Key Management – White Paper
- Enterprise Key Management Solutions – Solution Brief
- CipherTrust Cloud Key Manager Introduction -- Video
- Enterprise Key Management Solutions -- Solution Brief
How can you provide a clear path to comprehensive data security?
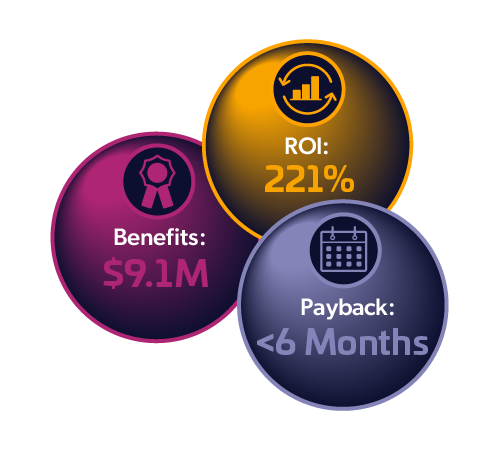
Total Economic Impact™ of Thales
CipherTrust Data Security Platform
Cost Savings and Business Benefits
Enabled by the CipherTrust Data Security Platform