What is Encryption Key Management?
Encryption is a process that uses algorithms to encode data as ciphertext. This ciphertext can only be made meaningful again, if the person or application accessing the data has the data encryption keys necessary to decode the ciphertext. So, if the data is stolen or accidentally shared, it is protected because it is indecipherable, thanks to data encryption.
Controlling and maintaining data encryption keys is an essential part of any data encryption strategy, because, with the encryption keys, a cybercriminal can return encrypted data to its original unencrypted state. An encryption key management system includes generation, exchange, storage, use, destruction and replacement of encryption keys.
According to Securosis’s White Paper, "Pragmatic Key Management for Data Encryption":
- Many data encryption systems don’t bother with “real” key management – they only store data encryption keys locally, and users never interact with the keys directly. Super-simple implementations don’t bother to store the key at all – it is generated as needed from the passphrase. In slightly more complex (but still relatively simple) cases the encryption key is actually stored with the data, protected by a series of other keys which are still generated from passphrases.
- There is a clear division between this and the enterprise model, where you actively manage keys. Key management involves separating keys from data for increased flexibility and security. You can have multiple keys for the same data, the same key for multiple files, key backup and recovery, and many more choices.
Best practice is to use a dedicated external key management system. There are four types1 :
1. An HSM or other hardware key management appliance, which provides the highest level of physical security
2. A key management virtual appliance
3. Key management software, which can run either on a dedicated server or within a virtual/cloud server
4. Key Management Software as a Service (SaaS)
Related Articles
Secure your data, comply with regulatory and industry standards, and protect your organization’s reputation. Learn how Thales can help.
- Unified Key Management Solutions
- Cracking the Confusion: Encryption and Tokenization for Data Centers, Servers and Applications by Securosis – White Paper
- Thales Key Management– White Paper
- Own and Manage your Encryption Keys– White Paper
- Best Practices for Cloud Data Protection and Key Management– White Paper
- Securing Microsoft Office365 and other Azure applications with CipherTrust Key Broker for Azure – White Paper
- The Importance of KMIP Standard for Centralized Key Management – White Paper
- Enterprise Key Management Solutions – Solution Brief
- CipherTrust Cloud Key Manager Introduction -- Video
- Enterprise Key Management Solutions -- Solution Brief
How can you provide a clear path to comprehensive data security?
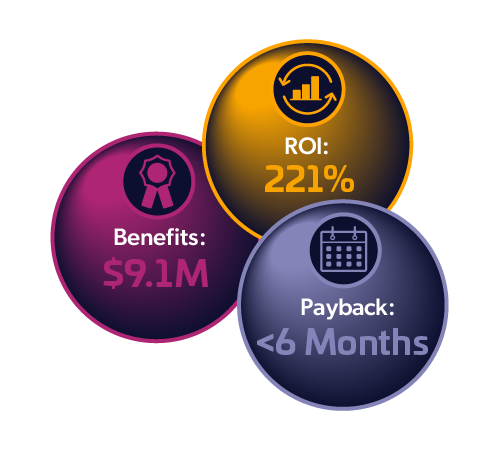
Total Economic Impact™ of Thales
CipherTrust Data Security Platform
Cost Savings and Business Benefits
Enabled by the CipherTrust Data Security Platform