What is the Encryption Key Management Lifecycle?
The task of key management is the complete set of operations necessary to create, maintain, protect, and control the use of cryptographic keys. Keys have a life cycle; they’re created, live useful lives, and are retired. The typical encryption key lifecycle likely includes the following phases:
- Key generation
- Key registration
- Key storage
- Key distribution and installation
- Key use
- Key rotation
- Key backup
- Key recovery
- Key revocation
- Key suspension
- Key destruction
Defining and enforcing encryption key management policies affects every stage of the key management life cycle. Each encryption key or group of keys needs to be governed by an individual key usage policy defining which device, group of devices, or types of application can request it, and what operations that device or application can perform — for example, encrypt, decrypt, or sign. In addition, encryption key management policy may dictate additional requirements for higher levels of authorization in the key management process to release a key after it has been requested or to recover the key in case of loss.
Related Articles
Secure your data, comply with regulatory and industry standards, and protect your organization’s reputation. Learn how Thales can help.
- Unified Key Management Solutions
- Cracking the Confusion: Encryption and Tokenization for Data Centers, Servers and Applications by Securosis – White Paper
- Thales Key Management– White Paper
- Own and Manage your Encryption Keys– White Paper
- Best Practices for Cloud Data Protection and Key Management– White Paper
- Securing Microsoft Office365 and other Azure applications with CipherTrust Key Broker for Azure– White Paper
- The Importance of KMIP Standard for Centralized Key Management– White Paper
- Enterprise Key Management Solutions – Solution Brief
- CipherTrust Cloud Key Manager Introduction-- Video
- Enterprise Key Management Solutions– Solution Brief
How can you provide a clear path to comprehensive data security?
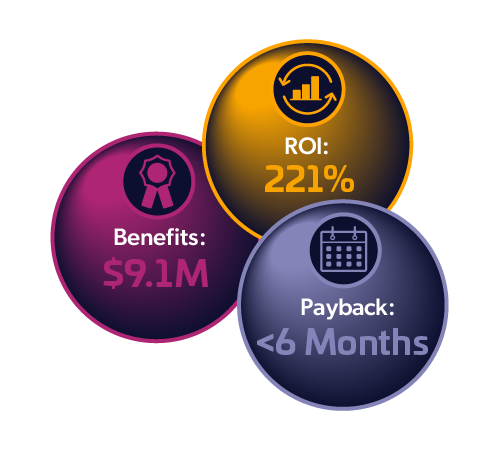
Total Economic Impact™ of Thales
CipherTrust Data Security Platform
Cost Savings and Business Benefits
Enabled by the CipherTrust Data Security Platform